VPN (Virtual Private Network) Definition: VPN meaning that it is a private point-to-point connection between two machines or networks over a shared or public network such as the internet. A Virtual Private Network is a combination of software and hardware. VPN (Virtual Private Network) technology, can be use in organization to extend its safe encrypted connection over less secure internet to connect remote users, branch offices, and partner private, internal network. VPN turn the Internet into a simulated private WAN.
It uses “virtual” connections routed through the internet from a business’s private network to the remote site. A Virtual Private Network is a technology which creates a network, and that network is virtually private.
The letter V in VPN stands for “virtual” means that it shares physical circuits with other traffic and it has no corresponding physical network.
For example, suppose there is a company which has two locations, one in Noida and other in Pune. For both places to communicate efficiently, the company has the choice to set up private lines between the two locations. Although private lines would restrict public access and extend the use of their bandwidth, it will cost the company a great deal of money since they would have to purchase the communication lines per mile. So, the more viable option is to implement a VPN. The company can hook their communication lines with a local ISP in both cities. Thus, the ISP would act as a middleman, connecting the two locations. This would create an affordable small area network for the company.
A VPN client uses TCP/IP protocol, that is called tunneling protocols, to make a virtual call to VPN server.
We’ll be covering the following topics in this tutorial:
What is VPN (Virtual Private Network)
Virtual private network extends a private network across public networks. VPN allows users working at home or office to connect in a secure fashion to a remote corporate server using the routing infrastructure provided by a public inter-network (such as the Internet). From the user’s perspective, the VPN is a point-to-point connection between the user’s computer and a corporate server. The nature of the intermediate inter-network is irrelevant to the user because it appears as if the data is being sent over a dedicated private link.

Types of VPN (Virtual Private Network)
VPN is of three kinds:
Remote access VPN (Virtual Private Network)
• The VPN which allows individual users to establish secure connections with a remote computer network is known as remote-access VPN.
• There is a requirement of two components in a remote-access VPN which are as follows:
I. Network Access Server (NAS)
II. Client software.
• It enables the remote connectivity using any internet access technology.
• Here, the remote user launches the VPN client to create a VPN tunnel.
Intranet VPN (Virtual Private Network)
• If a company has one or more remote locations and the company wants to join those locations into a single private network, then that company can create an intranet VPN so that they can connect LAN of one site to another one.
• Intranet VPN can link corporate headquarters, remote offices and branch offices over a shared infrastructure using dedicated connections.
• If we use intranet VPN, then it reduces the WAN bandwidth costs.
• The user can also connect new sites easily by using this network.
Extranet VPN ( Virtual Private Network)
• If a company has the close relationship with the other company (that company can be their customer, supplier, branch and another partner company), then those companies can build an extranet VPN so that they can connect LAN of one company to the other. It allows all of the companies to work in a shared environment.
• The extranet VPN facilitates e-commerce.
Type of VPN (Virtual Network Protocols)
There are three network protocols are used within VPN tunnels.That are:
Internet Protocol Security (IPSec)
We can make use of this protocol for encryption. It is used as a protocol suite. It is used as a “protocol suite for securing Internet Protocol (IP) communications by authenticating and encrypting each packet of IP of a data stream.” It requires expensive, time-consuming client installations, which is its most significant disadvantage.
Point-to-Point Tunneling Protocol (PPTP)
Generally, it is the most widely used VPN protocol among windows users. It was created by Microsoft in association with the other technology companies. The most significant disadvantage of PPTP is that it does not provide encryption. It relies on PPP (Point-to-Point Protocol). It is implemented for the security measures. It is also available for Linux and Mac users. As compared to other methods, PPTP is faster.
Layer 2 Tunneling Protocol (L2TP)
It is another tunnelling protocol which supports VPN. L2TP is created by Microsoft and Cisco as a combination between PPTP and L2F (Layer 2 Forwarding). L2TP also does not provide encryption as like as PPTP. The main difference between both of them is that L2TP delivers data confidentiality and data integrity.
Secure Socket Layer (SSL)
It is a VPN accessible via https over a web browser. Its most significant advantage is that it doesn’t need any software installed because it uses the web browser as the client application. With the help of SSL VPN, the user’s access can be restricted to specific claims instead of allowing access to the whole network.
Privacy, Security and Encryption
Data sent across the public Internet is generally not protected from curious eyes, but you can make your Internet communications secure and extend your private network with a virtual private network (VPN) connection. VPN uses a technique known as tunneling to transfer data securely on the Internet to a remote access.
The Internet connection over the VPN is encrypted and secure. New authentication and encryption protocols are enforced by the remote access server. Sensitive data is hidden from the public, but it is securely accessible to appropriate users through a VPN.
How to Setup a VPN
There are following two ways to create a VPN connection:
By dialing an Internet service provider (ISP)
If you dial-in to an ISP, your ISP then makes another call to the private network’s remote access server to establish the PPTP or L2TP tunnel After authentication, you can access the private network.
By connecting directly to the Internet
If you are already connected to an Internet, on a local area network, a cable modem, or a digital subscriber line (DSL), you can make a tunnel through the Internet and connects directly to the remote access server. After authentication, you can access the corporate network.
Equipment of VPN
Equipment having the VPN function includes routers and firewalls.Basically, communication is made via VPN equipment. Information is encrypted by the transmission VPN equipment before transmission and decoded by the receiving VPN equipment after receipt of information. The key for encrypt the data is set in VPN equipment in advance. The VPN equipment at receiving side decodes encrypted data before sending it to the receiving computer. 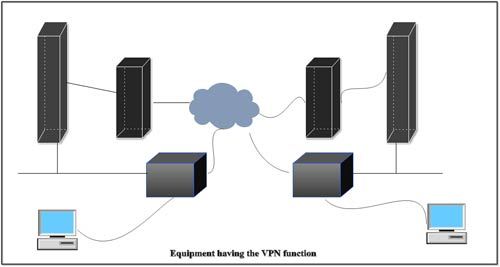 The advantages of encryption by way of cryptography may be looked into other services, such as
The advantages of encryption by way of cryptography may be looked into other services, such as
- Assuring integrity check: This ensures that undesirable person has not tampered data delivered to the destination during transmission.
- Providing authentication: Authentication authorizes the sender identity.
Features of a Typical VPN solution
When the remote offices connect each other to share vital resources and secret information, the VPN solution must ensure the privacy and integrity of the data as it traverses the Internet. Therefore, a VPN solution must provide at least all of the following:
Keep data confidential (encryption)
• Data carried on the public network must be rendered unreadable to unauthorized clients on the network.
Ensure the identities of two parties communicating (authentication)
• The solution must verify the user’s identity and restrict VPN access to authorized users only. It must also provide audit and accounting records to show who accessed what information and when.
• Safeguard the identities of communicating parties (tunneling)
• Guard against packets being sent over and over (replay prevention)
• Ensure data is accurate and in its original form (non-repudiation)
Address Management. The solution must assign a client’s address on the private net and ensure that private addresses are kept private.
Key Management. The solution must generate and refresh encryption keys for the client and the server.
Multiprotocol Support. The solution must handle common protocols used in the public network. These include IP, Internet Packet Exchange (IPX), and so on.
An Internet VPN solution based on the Point-to-Point Tunneling Protocol (PPTP) or Layer 2 Tunneling Protocol (L2TP) meets all of these basic requirements and takes advantage of the broad availability of the Internet. Other solutions, including the new IP Security Protocol (IPSec), meet only some of these requirements, but remain useful for specific situations.
Benefits of VPN
The main benefit of a VPN is the potential for significant cost savings compared to traditional leased lines or dial up networking. These savings come with a certain (in amount of risk, however, particularly when using the public Internet as the delivery mechanism for VPN data.
The performance of a VPN will be more unpredictable and generally slower than dedicated lines due to public Net traffic. Likewise, many more points of failure can affect a Net-based VPN than in a closed private system. Utilizing any public network for communications naturally raises new security concerns not present when using more controlled environments like point-to-point leased lines.
Getting Free VPN Services
A free VPNs some of the most useful online services on all devices that allows people to browse the Web securely.
Advantages of VPN (Virtual Private Network)
The benefits of VPN are as follows:
• Security: The VPN should protect data while it’s travelling on the public network. If intruders attempt to capture data, they should be unable to read or use it.
• Reliability: Employees and remote offices should be able to connect to VPN. The virtual network should provide the same quality of connection for each user even when it is handling the maximum number of simultaneous connections.
• Cost Savings: Its operational cost is less as it transfers the support burden to the service providers.
• It reduces the long-distance telephone charges.
• It cut technical support.
• It eliminates the need for expensive private or leased lines.
• Its management is straightforward.
• Scalability: growth is the flexible, i.e., we can easily add new locations to the VPN.
• It is efficient with broadband technology.
• By using VPN, the equipment cost is also reduced.
Disadvantages of VPN (Virtual Private Network)
The difficulties of VPN are as follows:
• For VPN network to establish, we require an in-depth understanding of the public network security issues.
• VPNs need to accommodate complicated protocols other than IP.
• There is a shortage of standardisation. The product from different vendors may or may not work well together.
• The reliability and performance of an Internet-based private network depend on uncontrollable external factors, which is not under an organisation’s direct control.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular