The word network protocol designates a set of rules or conventions to carry out a particular task. In data transmission, the network protocol is used in a less broad sense to indicate the set of rules or specifications that are used to implement one or more levels of the OSI model.
A network protocol defines that it communicates, how it communicates, and when it communicates. The critical elements of a network protocol are its syntax, its semantics and its timing.
Syntax: It refers to the structure of the data format, that is, the order in which they presented. For example, a simple network protocol could expect the first eight bits of data to be the sender’s address, the next eight bits, the receiver’s address and the rest of the flow to be the message itself.
Semantics: It refers to the meaning of each bit section. How do you interpret a specific pattern and action is taken based on that representation. For example, does an address identify the route to be taken or the final destination of the message?
Timing: It defines two characteristics: When the data should send and how quickly it should send. For example, if a sender produces data at a speed of 100Mbps, but the receiver can process data only at 1 Mbps, the transmission overload the receiver, and a large amount of data loss.
We’ll be covering the following topics in this tutorial:
Protocol Functions
Not all network protocols perform all functions, as it would imply a significant duplication of effort. There are several examples of the same type of functions present in network protocols of different levels.
The functions of the network protocols can group into the following categories:
Segmentation and assembly: It is when an entity (anything capable of sending or receiving information) of the application sends data in messages or a continuous sequence, lower level network protocols may need to divide the data into smaller blocks and all of it. For convenience, it is called a protocol data unit (PDU) to a block of data exchanging between two entities through a network protocol.
Encapsulated: Each PDU consists not only of data but also of control information. Instead, some PDUs contain only control information, no data. Control information classified into three categories:
• Address: you can indicate the address of the sender and the receiver.
• Error address code: sometimes some frame check sequence is included for error detection.
• Protocol control: additional information is included to implement the network protocol functions listed in the rest of this section.
Connection Control: An entity can transmit data to another entity so that each PDU is treated independently of the previous PDUs. It is known as the transfer of non-connection oriented data; An example is the use of datagrams. Although this mode is useful, an equally important technique is the transfer of connection-oriented data, of which the virtual circuit is an example.
If the stations provide for an extended exchange of data and some details of their network protocol change dynamically, it is preferable (even necessary) for the transfer of connection-oriented data. A logical association, or connection, is established between entities.
• Connection establishment
• Data transfer
• Connection release
Shipping ordered: If two communicated entities are at different stations in a network, there is a danger that the PDUs will not be received in the same order in which they send because they follow different paths through the network. In connection-oriented protocols, it is generally necessary that the order of the PDUs be maintained. For example, if you transfer a file between two systems, we would like to be sure that the records of the received file are in the same order as those of the transmitted file, and not mixed. If each PDU has a unique number, and the numbers are assigned sequentially, the reordering of the PDUs received based on the sequence numbers is a simple logical task for the receiving entity. The only problem with this scheme is that the sequence numbers repeated due to the use of a finite field of sequence numbers (module some maximum number).
Flow control: Flow control is a function performed by the receiving entity to limit the amount or rate of data sent by the issuing entity.
The purest form of flow control is a stop-and-wait procedure, in which each PDU must confirm before the next one sent. The use of more efficient network protocols implies the use of some form of credit offered by the issuer, which is the amount of data that can send without confirmation.
Error control: The use of techniques to manage the loss or errors of data and control information is necessary. Most of the techniques include error detection, based on the use of a frame check sequence, and PDU re-transmission.
Addressing: The concept of addressing in a communications architecture is complex and encompasses a large number of concepts such as the level of addressing, scope of the address, connection identifiers and mode of address.
Multiplexing: Multiplexing is related to the concept of addressing. In a single system, a form of multiplexing supported through multiple connections. For example, with X.25, there can be multiple virtual circuits that end in the same final system; It can say that these virtual circuits multiplexed on the physical interface between the final system and the network.
Transmission services: A network protocol can offer a wide variety of additional services to entities that make use of it. Three common examples are the priority, degree of service and safety.
The most common network protocols
The network protocol determines the mode and organization of the information (both data and controls) for transmission through the physical medium with the low-level protocol. The most common network protocols are:
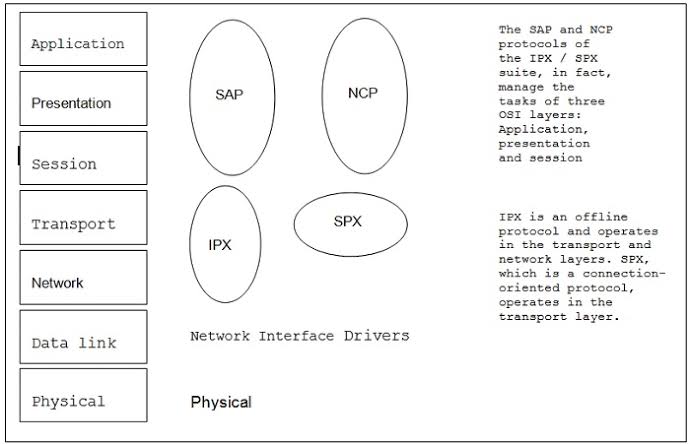
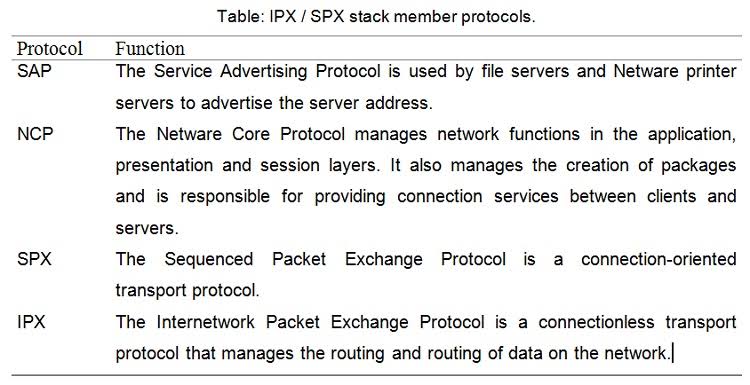
IPX/SPX
IPX / SPX (Internetwork Packet Exchange / Sequenced Packet Exchange) is a set of network protocols developed by Novell to used in your Netware network operating system. IPX / SPX groups fewer protocols than TCP / IP, so it does not require the same general load that TCP / IP needs. IPX / SPX can be used in both small and large networks and allows data routing.
NetBEUI
NetBEUI (NetBIOS Extended User Interface) is a fast and straightforward network protocol that was designed to use in conjunction with the NetBios protocol (Net-Ware Basic Input Output System) developed by Microsoft and IBM for small networks. NetBEUI operates in the Transport layers of the OSI Model.
Since NetBEUI only provides the services that required in the OSI transport and network layers, it needs to work with NetBios that operates in the OSI model layer and is responsible for establishing the communication session between the 2 computers connected to the net. Microsoft networks also include two other components: the redirector and the Server Message Block. The re-director operates at the application layer and makes a client computer perceive all network resources as if they were local. The server message block (Server Message Block or SMB) for its part, provides same-level communication between the re-directors included in the client machines and network server. The server message block operates in the presentation layer of the OSI model.
Although it is an excellent low-cost transport protocol, NetBEUI is not a protocol that can route through routers, so it cannot use in-network interconnections. Therefore, while NetBEUI is a network protocol option for small and simple networks, it is not valid for more extensive networks that require the use of routers.
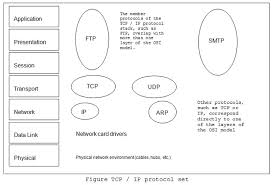
TCP / IP
Often referred to as the “low bid protocol” TCP / IP has become the de facto standard for corporate network connection. TCP / IP networks are widely scalable, so TCP / IP can be used for both small and large networks.
TCP / IP is a set of routing protocols that can run on different software platforms (Windows, Unix, etc.) and almost all network operating systems support it as the default network protocol. TCP / IP consists of a series of member protocols that make up the TCP / IP stack. And since the set of TCP / IP protocols developed before the OSI reference model completed, the protocols that comprise it do not correspond correctly with the different layers of the model.
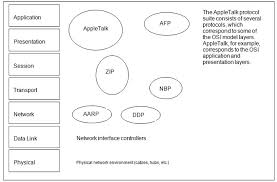
APPLETALK
This protocol is included in the Apple Macintosh computer operating system since its inception and allows computers and peripherals to be interconnected with great simplicity for the user, since it does not require any configuration, on the other hand, the operating system takes care of everything. Although many network administrators do not consider AppleTalk a corporate or interconnect network protocol, AppleTalk allows data routing through routers. AppleTalk can support Ethernet, Token Ring, and FDI network architectures.

 [/vc_column_text][/vc_column][/vc_row]
[/vc_column_text][/vc_column][/vc_row]
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular