In the 1970s, the Department of Defense, or DOD (Department Of Defense), decided before the proliferation of machines using different, incompatible communication protocols, to define its own architecture. This architecture, called TCP / IP, is the source of the Internet. It is also adopted by many private networks, called intranets.
The two main protocols defined in this architecture are:
• IP (Internet Protocol) network level, which provides connectionless service.
• TCP (Transmission Control Protocol) transport level, which provides a service with reliable connection.
TCP / IP define a layered architecture that also includes, without being explicitly defined, an access interface to the network. Indeed, many separate subnets can be taken into account in the TCP / IP architecture, both local type than extended.
This architecture is illustrated in FIG. Note in this figure the appearance of another level protocol message (layer 4), UDP (User Datagram Protocol). This protocol uses a connectionless mode, which allows you to send messages without the recipient’s permission.
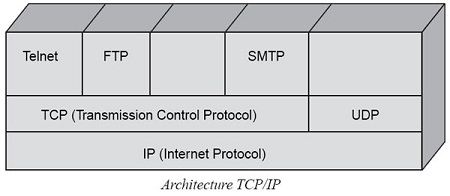
This architecture for base IP, which corresponds to the packet level (Layer 3) of the architecture of the reference model. In reality, it corresponds only partially at this level. The IP protocol was designed as interconnection protocol defining a data block of a well defined format and containing an address but no other functionality. Its role was to carry that data block in a package according to any other packet transfer technique. This applies to the first generation of IP, called IPv4, which is still heavily used today. The second version of the IP protocol, IPv6, actually plays a role level package, with new features to transport packets from one end of the network to another with some security.
IP packets are independent of each other and are routed individually within the network through routers. The quality of service offered by IP is very low, without detection of lost packets or possibility of error recovery.
TCP includes message-level features (layer 4) of the reference model. This is a fairly complex protocol, which has many options to solve all the problems of packet loss in the lower levels.
In particular, a lost fragment can be recovered by retransmission on the flow bytes. TCP is connection-oriented mode, unlike UDP. This Last UDP is also positioned at the transport level but in a connectionless and offers virtually any functionality. It can not be considered as applications that require little service from the transport layer.
Protocols located above TCP and UDP application type and are derived largely from the UNIX world.
The power of this architecture is based on the flexibility of its implementation over any existing network. So, for example, X and Y, respectively, a local network and a wide area network to switch cells or packets. The IP protocol is implemented on all machines connected to both networks. To make it possible to move from one network to another, router, whose role is to uncap the packet came from the X network and retrieve the IP packet is set up. After treatment, mainly routing, the IP packet is encapsulated in the packet network Y. The role of the router is, as its name suggests, routing the packet to the correct destination.
The Internet network interconnect architecture is illustrated in Figure.
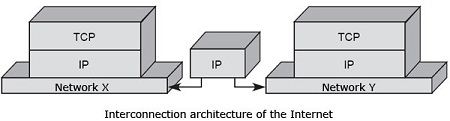
The flexibility of this architecture can sometimes be a default, in the sense that the overall network optimization is performed subnet by subnet, that is to say, it is obtained by a succession of local optimizations .
An important feature of the TCP/IP architecture is that intelligence and network control are almost entirely in the terminal machine and not in the network, at least for IPv4. It is the TCP protocol which is responsible for sending more or fewer packets in the network according to the occupation thereof. The control intelligence is in the PC end, specifically in the TCP software. The TCP window control increases or decreases the traffic according to the speed required to make a return. The cost of infrastructure is extremely low because many software and therefore most of the intelligence, are in terminal machines. The service rendered by this network of networks of best-effort type, which means that the network does its best to carry the traffic.
IPv6 brings a new dimension, since it introduces new features that make the nodes of the network smarter. The new generations of routers have QoS management algorithms to ensure a transport capable of meeting timing constraints or packet loss. However, IPv4 has responded well to novel aspects of IPv6, modifying some fields to offer the same improvements.
In the classic version of IPv4, each new customer is not treated differently from those who are already connected, and resources are distributed fairly among all users. Resource allocation policies of the telecom operators are totally different, a customer already has a certain quality of service that should not be penalized by the arrival of a new customer. As we shall see, the now advocated solution in the Internet environment is to ensure, to the extent possible, customers with real-time requirements, and by appropriate protocols.
The applications available over the TCP/IP environment are many and varied. They include email (SMTP), file transfer it (FTP) and especially the databases distributed with the World-Wide Web (WWW).
The set of TCP / IP protocols structured in 5 functional levels:
Physical Level
The physical level corresponds to the hardware. It can be a coaxial cable, a twisted pair cable, fiber optic cable or a telephone line. TCP / IP does not officially consider the physical level as a specific component of its model and tends to group the physical level with the network level. The main protocols of this level are ARP and RARP.
Network Level
The network-level Regardless of the physical medium used, you need a specific network card that, in turn, depend on software called a device driver provided by the operating system or by the manufacturer. It provides reliability (although not necessarily) in the distribution of data that different formats can adopt. Although TCP / IP does not specify any protocol for this level, the most notable protocols are SLIP, PPP, and PPTP.
Internet level
The Internet level overlaps the physical network creating a virtual network service independent of it. It is not reliable or connection-oriented. It is responsible for addressing and routing the data to the receiving station. The specific protocol of this level is IP. The protocol does not take into account the reliability of the data, its ordering, or other network needs. It merely provides an addressing scheme and a mechanism to fragment packets and transmit them over networks that allow reduced frame sizes.
Each frame of information that is processed by this level is considered a separate and unique element. There is no concept of continuous connection. The IP module takes the data from the TCP module, applies the corresponding addressing information to the data, and sends it to the network level. IP implements its method of error verification, using a checksum of the data, which sent with each packet. A checksum is a simple numerical sum of the data that has to be verified. If a receiving device observes that the checksum evaluated differs from that contained in the frame, it discards the frame.
The IP module is responsible for managing packet fragmentation when necessary. It is necessary to fragment when the packets that move, from an extensive network to another whose data size has a lower limit, when fragmentation takes place, information about the origin and destination copied into each of the new packages created. The information necessary for the receiving device to assemble the fragmented packets and form the original sequence also stored in each of them. Each packet contains an IP header, which stores the information elements of the packet.
The IP header contains the following fields, which defined below: version, IHL, type of service, total length, identification, markers, fragment shift, lifetime, protocol, header checksum, source address, a destination address, options, and padding Figure.
• Version: This field provides information about the version of IP that was used to build the package. The current standard is IP version 4. Later we discuss the new IP v.6 and the benefits it offers over the current standard.
• IHL: This number is the total length of the header, in units of 4 bytes. The minimum length of an IP header is 5, or a total of 20 bytes.
• Type of service: This field allows you to request a certain quality in the transmission. Depending on the type of network the data is traveling through, this field can be used or ignored. For example, by appropriately configuring this field, qualities such as High Through-put (high performance) or High Reliability (high reliability) can be requested.
• Total length: the total length of the package that sent.
• Identification: Used to assemble fragmented packages.
• Indicators: These indicators are used to determine if a package is a fragment of a larger package, or if it can be fragmented.
• Lifetime: As we mentioned earlier, this byte represents the “waiting time” in a package. It consists of a single byte, which stores a specific number in seconds. In each device through which the packet passes, a gateway, for example, this value must be decremented by at least one unit.
• Protocol: This field indicates the protocol used in the data part of the package.
• Header checksum: Again, this number represents a verification, which ensures that the information contained in the header remains unchanged.
• Source / Destination address: These digits constitute our 32-byte IP addresses, to identify the machines through the different segments of a network.
• Options: The options may contain various data, among others, routing information. It is possible to keep track of the route a package takes, as it travels through the network, setting an option in this field.
• Fill: The IP header must be divisible into units of 4 bytes (32 bits). To ensure that the header meets this condition, zeros a added at the end of it.
Transportation Level
The transport level provides applications with communications services from the sending station to the receiving station. It uses two types of protocols: TCP that is reliable and connection-oriented and UDP that is unreliable and not connection-oriented.
TCP
The TCP (Transmission Control Protocol) protocol is IP based that is unreliable and not connection-oriented, and yet it is:
Connection-oriented It is necessary to establish a previous connection between the two machines before any data can be transmitted. Through this connection, the data always reach the destination application in an orderly manner and without duplicates. Finally, it is necessary to close the connection.
The TCP protocol allows reliable communication between two applications. In this way, the applications that use it do not have to worry about the integrity of the information: they assume that everything they receive is correct.
The data flow between one application and another travel through a virtual circuit. We know that IP datagrams can follow different routes, depending on the state of intermediate routers, to reach the same site. It means that the IP datagrams that carry the messages follow different routes although the TCP protocol achieved the illusion that there is a single circuit through which all the bytes travel one after the other (something like a pipe between the origin and the destination). For this communication to be possible, it is necessary to open a connection beforehand. This connection ensures that all data arrives correctly in an orderly manner and without duplicates. The data unit of the protocol is the byte so that the source application sends bytes, and the destination application receives these bytes. However, each byte is not sent immediately after being generated by the application but is expected to have a certain number of bytes, it grouped into a segment, and the entire segment sent. For this, intermediate memories or buffers are necessary. Each of these segments travels in the data field of an IP datagram. If the segment is vast, it necessary to fragment the datagram, with the consequent loss of performance; and if it is small, more headers than data sent. Therefore, it is essential to choose the most significant possible segment size that does not cause fragmentation.
The TCP protocol sends an unstructured flow of information. It means that the data does not have any format; it is only the bytes that one application sends to another. Both applications must agree to understand the information they are sending.
Each time a connection opened, a two-way communication channel created in which both applications can send and receive information, that is, a connection is full-duplex.
UDP
UDP provides the primary mechanism that application programs use to send datagrams to other application programs. UDP provides protocol ports used to distinguish between many programs that run on the same machine. That is, in addition to the data, each UDP message contains both the destination port number and the source port number, making it possible for the UDP software at the destination to deliver the message to the correct recipient and send it a reply.
UDP uses the underlying Internet Protocol to transport a message from one machine to another and provides the same semantics of datagram delivery, offline and unreliable as the IP. It does not use acknowledgments to ensure that messages arrive; it does not order incoming messages, nor does it provide feedback to control the speed of information flow between machines. Therefore, UDP messages can be lost, duplicated, or arrived without order. Also, packets can arrive faster than the receiver can process them. In summary: UDP provides an offline and unreliable delivery service, using the IP to transport messages between machines. It uses IP to carry messages but adds the ability to distinguish between several destinations within the host computer.
UDP message format:
The header divided into four 16-bit fields, which specify the port from which the message sent, the port to which the message intended, the length of the message, and a UDP checksum.
Application Level
The application-level corresponds to the applications available to users such as FTP, SNMP, TELNET, etc.
Programs that run at the application level are also usually extended to the presentation level. They usually implement both the user interface and the language to which the interface translates the data to be able to speak on the network. In some operating systems, the OS may provide certain vital functions, such as the ability to communicate with email servers, etc.
Each UDP message is known as a user datagram. Conceptually, a user datagram consists of two parts: a UDP header and a UDP data area.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular