This section presents an overview of the most common protocols used for TCP/IP communication. The discussion focuses on the nature of these applications and the purpose they serve.
We’ll be covering the following topics in this tutorial:
The Client/Server Model
TC/IP applications operate at the application or process layer of the TCP/IP hierarchy as discussed in the preceding sections. TCP/IP protocol splits an application into server and client components. The server component is a service provider that controls commonly shared resources pertaining to a particular application on the network. The server normally runs on a remote, high-powered, computer to which only authorized users have access. The client component is the service user. That piece of software engages with the server in a sequence of request-response data grams fulfilling certain user-specified demands or requirements.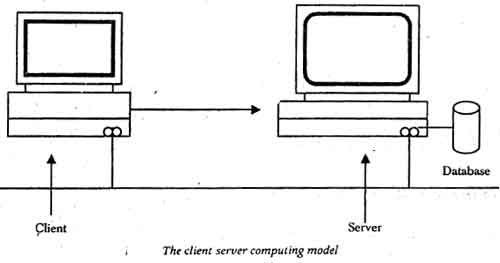
The client/server computing model has the following attributes;
Flexible deployment This can be easily customized.
Low computer cost Reduced processing requirement at the client end. In most cases, the client has to deal with lesser details of the application compared to the Server. This, in turn,. Means cheaper hardware on the client machine (less CPU power, memory, disk space, and so on). On the other hand, the server must be powerful enough and well-outfitted to make it respond satisfactorily to the user demands on its services.
Increased network management costs Reduced loss of bandwidth from unnecessary data traffic, due to the exchange of data on an as-needed basis. In the case of an Ethernet LAN, this also contributes to reduced collisions and therefore, better networks availability.
Lower transmission facility costs.
Telnet
Telnet is a program that allows a user with remote login capabilities to use the computing resources and services available on the host. Telnet can also be used to connect other ports serving user defined as well as well-known services. The telnet program requires two arguments that is the name of a computer on which the server runs and the protocol port number of the server. Telnet service is unique in that it is not platform-specific like other TCP/IP services. A DOS user running Telnet, for example, can connect to a UNIX host or a mainframe computer. The 90wn side of using Telnet, however, is that unless the user is familiar with the operating system running on the remote platform, he or she cannot use the desired resources easily.
File Transfer Protocol (FTP)
File Transfer protocol is among the oldest protocols still used in the internet. ITP is widely available on almost all-computing platforms, including DOS, OS/2, UNIX, and up to the mainframe level. ITP is a file server access protocol that enables a user to transfer files between two hosts across the network or Internet. This is also established through TCP. Accessing ITP sites over the internet requires that the user must have the knowledge of the location and the name of the desired files.
Unlike Telnet, ITP does not require any familiarity with the remote operating system. The user is still required, however, to be familiar with the ITP command set built into the protocol itself so that he or she can productively manage the session.
Modem FTP servers known as ftpd support two modes, the classic normal mode and more security conscious passive mode or PASV mode.
Trivial File Transfer Protocol (TFTP)
TITP, like ITP, is also an internet service intended for the transfer of files between hosts. Unlike ITP, however, TITP does not rely on TCP for transport services. Instead, TITP uses UDP to shuttle the requested file to the TITP client.
Simple Mail Transfer Protocol (SMTP)
The Simple Mail Transfer Protocol is an electronic mail (e-mail) service provider. It is intended for the Transfer of e-mail messages across ·the network. SMTP uses TCP transport for the reliable delivery of mail messages. When there is an outgoing mail, the SMTP client will connect to the SMTP server and sends the mail to the remote server.
Network File System (NFS)
Network File System service enables hosts across the network to share file system resources transparently among themselves. Although it all started on UNIX platforms, NFS can be implemented on any platform, including DOS, NetWare, and Windows NT.
Simple Network Management Protocol (SNMP)
Using the Simple Network Management Protocol, LAN administrators can monitor and tune the performance of TCP/IP (as well as non-TCP/IP) networks. Using SNMP, all kinds of information about network performance can be gathered, including statistics, routing tables, and configuration-related parameters. The information and configuration gathering capabilities of SNMP make it an ideal tool for network troubleshooting and performance tuning.
Domain Name System (DNS)
Due to Internet explosion, it is not practical to keep an exhaustive hosts file for every host because of the sheer volume of listing as well as addition, deletion and updating of new, old and current hosts. Therefore, DNS is used to provide host-to-IP address mapping of remote hosts to the local hosts and vice versa. As we know that each device connected directly to the network must have an IP address that is uniquely assigned to it. The address takes the form of a dotted decimal notation such as 128.45.6.89
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular