We’ll be covering the following topics in this tutorial:
What is an Incident?
An incident in the parlance of information security is a security breach or even an attempt to breach security. An unsuccessful attempt to crack the security system is also an incident and needs to be investigated thoroughly.
Incident Response Process
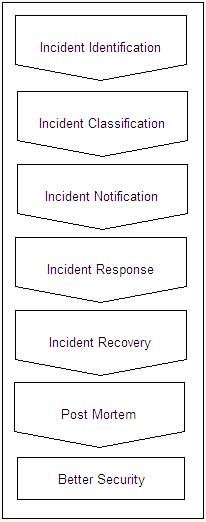
Whenever an incident takes place, a series of steps needs to be taken to find out the causes of the incident to ensure that such incidents do not occur in future. The incident response process involves the following steps:
- Incident identification – it is the first step of incident response in which the incident is identified. Some common incidents may be DoS, port scanning, IP sniffing, social engineering, banner capture, unauthorized access or virus infection.
- Incident classification – it is the next step in which the incident is classified based on its severity. Every organization must maintain an incident classification chart to rate an incident when it occurs based on its criticality.
- Incident notification – it is the notification given to specific functionaries about the incident.
- Incident response and containment – it is the action taken to thwart the incident.
- Incident recovery – it is the recovery activity to restore system to the previous status.
- Post mortem – this is the post incident investigation to find out the vulnerabilities in the system that allowed the incident to happen.
Some Attack Techniques and Technologies
Some of the attack tools and techniques are:
- IP spoofing is a the techniques of using forged 12 digit IP address (source) in the IP packets that are used in TCPIIP protocol for data communication (primarily on the Internet or on any other TCP/IP network) for concealing the identity of the sender or impersonating another computing system.
- Packet sniffing is a technique or a program to troubleshoot network traffic. However, often it is used by hackers to get information about the source and destination of IP packets on a TCP/IP network. When on a TCP/IP network like Internet, data is broken down into small packets that are transmitted over the network and gather together at the destination, reassembled and displayed/stored etc. these packets have stamps of destination and source on them so that they are not lost. Packet sniffing is the technique of that can capture these floating packets on the TCP/IP network like a wiretap and find out what is being sent to or from a source or destination.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular