To perform software maintenance effectively, various techniques are used. These include software configuration management, impact analysis, and software rejuvenation, all of which help in maintaining a system and thus, improve the quality of the existing system.
We’ll be covering the following topics in this tutorial:
Software Configuration Management
Software configuration management can be used effectively while maintaining a system as it keeps track of changes and their effects on the system components. Many changes occur when the software is delivered to the users such as failure or users’ request for enhancement in the software. For this, configuration control board (CCB) oversees the entire change process. Note that the representatives of CCB along with the users and developers manage changes collectively. These changes are managed in the following steps.
- When the user encounters a problem such as failure report, he requests for change on a formal change request form. The problem can also be an enhancement to a function, variation in the older function, or deleting an existing function. The procedure for request of change remains the same. The change reqest form should include information about how the system works, nature of the problem, and how the new (expected) system should work.
- The request for change is reported to CCB.
- The representative of CCB meets the user to discuss the problem (That is, to determine that the request is for failure report or for enhancement).
- If the user requests for a reported failure, the CCB discusses the source of the problem. If the requested change is an enhancement, the CCB discusses the parts or the components that will be affected by the change. In both the cases, developers describe the scope of changes and the expected time to implement them.
- The developers determine the source of the problem or the components which will be affected when the changes will be implemented. For this, they use a test copy instead of the operational system and implement the requested changes to see whether it (test copy) performs according to the requested changes.
- Finally, after the changes have been made, all the relevant documentation is updated according to the requested change.
- The developers then record all the changes made to the operational system in a change report to keep track of the next release or version of the software system.
Version control implies the process by which the contents of the software, hardware, or documentation are revised. It tracks and manages the progress of files and directories within a project. This process is required when one or more components of a software system are changed (for example, Microsoft has introduced MSN Messenger 7.0, which is an upgraded version of MSN Messenger 6.2). Software maintenance manages the versions, that is, the older version (present software) and the new version (when the software is modified). Note that the software configuration management manages how the versions differ, who made the changes, and why they were made.
The component (existing version) is assigned an identification number. When the version (current) is revised, a revision number is allotted to each resulting changed component. The records such as name of the component, date and time, version status, and account of all changes are managed. This helps the software configuration management to identify the current version and the revised number of the operational system.
Impact Analysis
Impact analysis is used to evaluate the overall effect of the requested change. This includes identifying the components that will be affected with the change, the extent to which each of the components will be affected, and the consequences of change on the estimated effort and schedule. There are various advantages of performing impact analysis, which are listed below.
- It is used to understand the situations when the modifications required in the software system affect large segments of software code or several components of the software.
- It helps identifying the relationship among the components that are affected with the change and thereby helping to understand the overall software structure.
- It is used to record the history of modification, which helps in maintaining quality in the software system.
Software Rejuvenation
Sometimes, organizations have to take difficult decisions about how to make their systems more maintainable. The choices may include enhancing or completely replacing a software system. Note that each choice has the same objective, that is, to preserve or increase the software quality while keeping the costs low. Software rejuvenation is a maintenance technique which helps in taking appropriate decisions.
Software rejuvenation checks the system’s work products in order to extract additional information or to reformat them in order to make these work products more understandable. Generally, four types of software rejuvenation exist, namely, re-documentation, restructuring, reverse engineering, and reengineering.
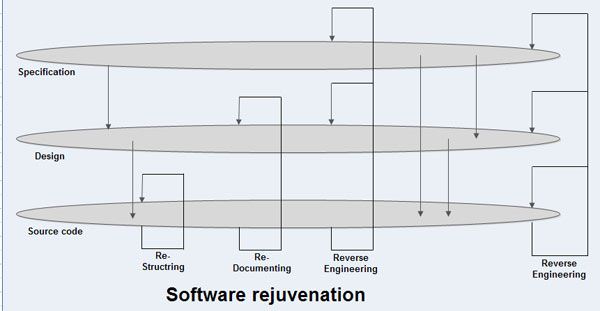
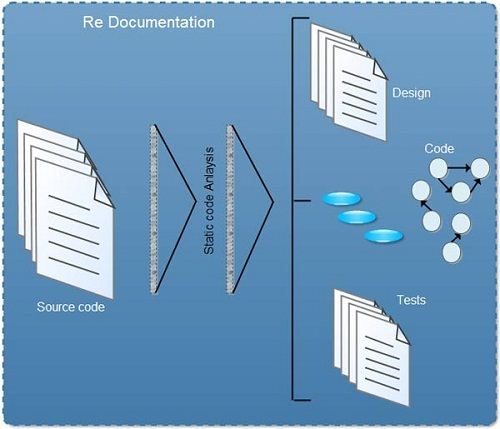
Re-documentation uses static analysis of the source code to produce additional information, which helps the software maintenance team to understand and refer to the code. In source code, component size, component calls, calling parameters, and control paths are examined to understand what and how code does it. The output of static code analysis is either graphical or textual, which can be used to assess whether the re-documentation is required.
Restructuring
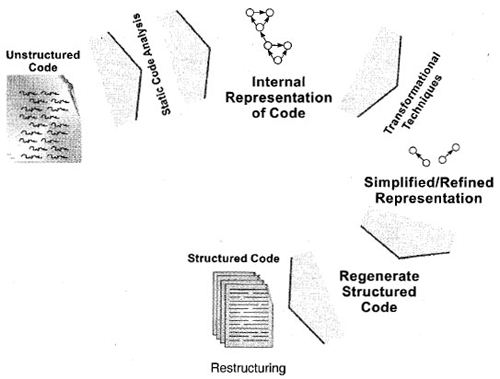
Restructuring involves the transformation of unstructured code into structured code thereby making it easier to understand and change. Restructuring involves the following steps.
- Static analysis is performed, which provides information that is used to represent code as a directed graph or associative (semantic) network. The representation mayor may not be in a human readable form; thus, an automated tool is used.
- Transformational techniques are used to refine (simplify) the representation.
- Refined representation is interpreted and used to generate the structured code.
Reverse Engineering
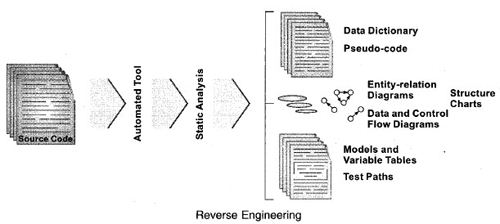
Reverse engineering like re-documentation, focuses on providing information about the specification and design information using the software code. The information extracted from specification and design is stored in a format that can be easily modified. Reverse engineering is a useful technique when the software maintenance team is unable to understand the processes involved in the software system. Reverse engineering involves the following steps.
- Source code is collected with the help of an automated tool used for reverse engineering. This tool is used to represent the structure and the naming information of variables, functions and other components in the software code.
- Static analysis is performed.
- Some methods such as standards structured analysis and design methods are used. These methods are used to extract information such as data dictionaries, data-flow, control flow, and entity relationship (ER) diagrams for the reverse engineering technique.
The advantages associated with reverse engineering are listed below.
- It focuses on recovering the lost information from the programs.
- It provides the abstract information from the detailed source code implementation.
- It improves system documentation ‘that is either incomplete or out of date.
- It manages the complexity that is present in the software programs.
- It detects the adverse effects of modification in the software system.
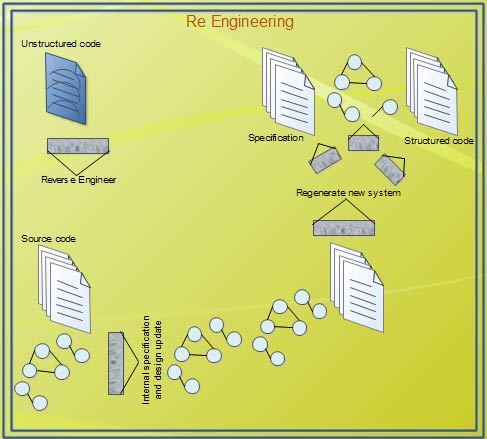
Re-engineering
Re-engineering is an extension of reverse engineering. This technique refers to the systematic transformation of the present software system into a new form to make quality improvements in operation, system capability, functionality, and achieving high performance at low costs.
Re-engineering involves the following steps.
- The system is reverse engineered and represented internally for human and computer modifications.
- The software system is corrected and completed. This includes updating internal specification and design.
- Using new specification and design, a new system is generated.
The advantages associated with re-engineering are listed below.
Reduced cost: Generally, it is observed that the software systems that are maintained using re-engineering incur less cost as compared to developing the software system all over again.
Reduced risk: The incremental nature of re-engineering means that the existing staff skills evolve as the software system evolves. Due to this fact, the risks associated with the modifications in the software system are reduced.
Better use of existing staff: The individuals who worked on software maintenance can be retained while the re-engineering technique is being used. In addition, the staff can be extended to accommodate new skills during reengineering. Due to this fact, the re-engineering technique has less number of risks and incurs less expenditure while hiring the new staff.
Incremental development: Re-engineering techniques can be carried out in stages according to the availability of budget and resources. This technique is useful in operational organizations with working software systems. In such organizations, the staff can easily adapt to the re-engineered software system.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular