The ISO/IEC 27001 definition of information defines information as an ‘asset’. Therefore, information is something that has value and requires to be protected against theft or destruction. In order to protect information from theft or destruction, all counter measures that are taken come under the purview of Information security measures. Information security is therefore defined as all steps taken by the organization to protect its information and information systems. The steps may be technical or managerial in nature and may involve automation or manual controls.
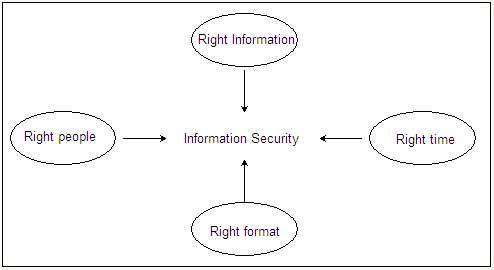
At the core of the concept of information security lies the concept of 4R which are
- Right information-means that information has to be accurate and complete
- Right people-means that information is available to the people who are authorized to receive it.
- Right time-means information must be available to the authorized individual on demand.
- Right format/form-means that information must be given in a format that makes some meaning. It has to be given in a format that makes decision-making easier.
If information has to be protected, the 4Rs must be applied properly, information and its value must be well understood and the threats to it must be analyzed in detail. Only then, can counter measures be taken to ensure that there is no deviation from the principles of the 4R, i.e., information confidentiality is maintained, information integrity is guaranteed, availability to authorized personnel is ensured on demand and the integrity of the formats of information storage and delivery are not tampered with.
However, there are risks to information assets. While some risks may be eliminated, some risks can only be minimized. Such risks are to be managed properly to ensure smooth functioning of the information infrastructure. From a security perspective, risks are potential issues and have to be understood carefully in order to come up with security counter measures that would minimize or eliminate the risk.
Risk may be defined by the formula as:
Risk =ƒ (Information asset value, threats, vulnerabilities)
As one can see, risk to an information system can be defined as a function of the asset value of the information, the threat to the information and its vulnerabilities. Risk can therefore be managed if we are able to manage the asset value, the threat to it and its vulnerabilities.
The risk management alternatives therefore are:
- Risk reduction.
- Risk acceptance.
- Risk transference.
- Risk avoidance.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular