• Computer Security means to protect information. It deals with prevention and detection of unauthorized actions by users of a computer.
• In simple words security is defined as “Protecting information system from unintended access”
• Security of information system refers to protecting all components of information system, specifically data, software, hardware and networks.
• Network security measures are needed to protect data during their transmission and to guarantee that data transmissions are authentic.
Network Security Threats
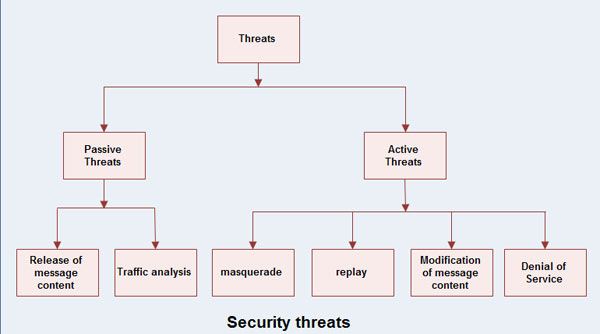
Network security threats fall into two categories
1. Passive threats
(a) Release of message contents
(b) Traffic analysis
2. Active threats
(a) Masquerade
(b) Replay
(c) Modification of message contents
(d) Denial of service
• Passive threats, sometimes referred to as eavesdropping dropping, involve attempts by an attacker to obtain information relating to communication.
(a) Release of message contents
• A telephone conversation, an e-mail message and a transferred file may contain sensitive or confidential information.
• We would like to prevent the opponent from learning the content of these transmissions.
(b) Traffic analysis
• It is a kind of attack done on encrypted messages.
• The opponent might be able to observe the pattern of such encrypted message.
• The opponent could determine the location and identity of communicating hosts and could observe the frequency and length of messages being exchanged .
• Active threats involve some modification of the data stream or the creation of a false stream.
(a) Masquerade
• It takes place when one entity pretends to be a different entity.
• A masquerade attack usually includes one of the other forms of active attack.
• For e.g. authentication sequences can be captured and replayed after a valid authentication sequence has taken place, thus enabling an authorized entity with few privileges to obtain extra privileges by impersonating an entity that has those privileges.
(b) Replay
• It involves the passive capture of a data unit and its subsequent retransmission to produce an unauthorized effect.
(c) Modification of message
• It means that some position of a message is altered, or that messages are delayed or rendered, to produce an unauthorized effect.
(d) Denial of service (DOS)
• A denial of service attack takes place when the availability to a resource is intentionally blocked or degraded by an attacker.
• In this way the normal use or management of communication facilities is inhibited.
• This attack may have a specific target. For e.g. an entity may suppress all messages directed to a particular destination.
• Another form of service denial is the disruption of an entire network, either by disabling the network or by overloading it with messages so as to degrade performance.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular