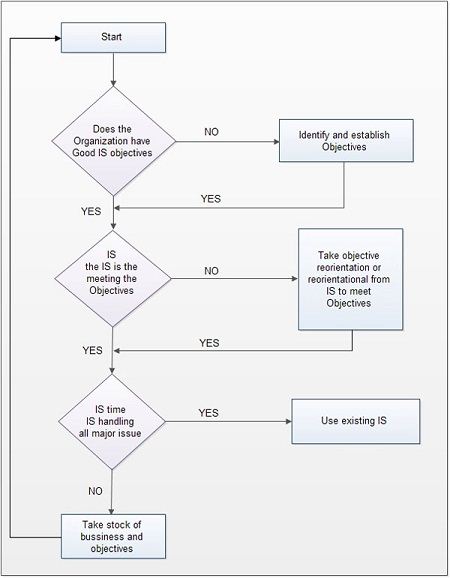
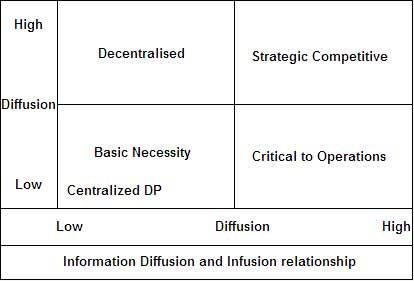
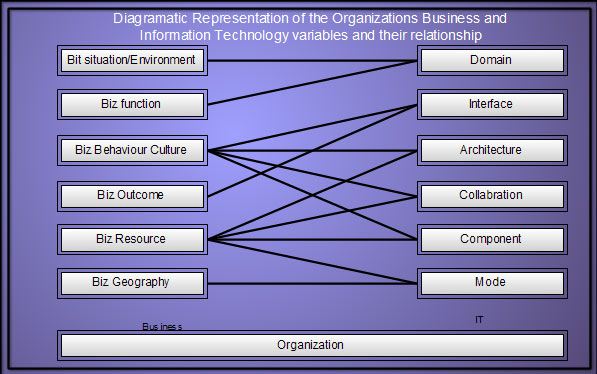
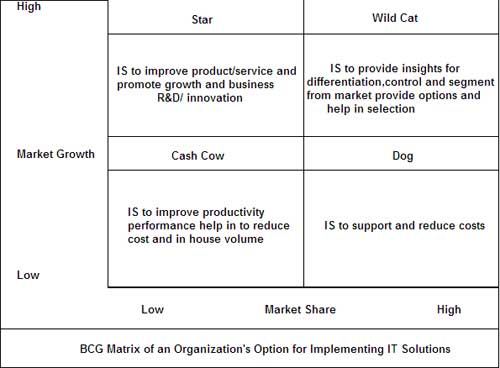
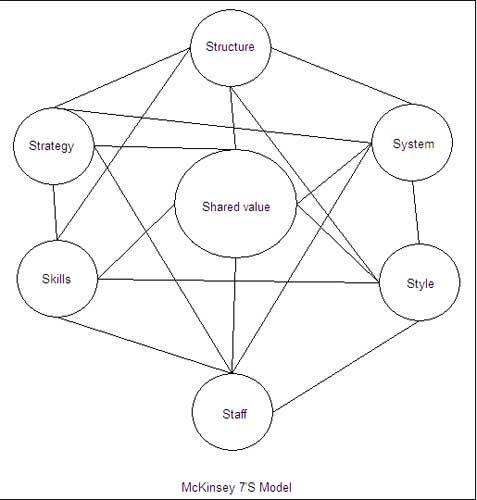
Ethics is a branch of philosophy that deals with what is considered right and wrong in society. It deals with issues which are not in the realm of legal or statutory domains but which may be considered conventionally right or wrong as per perception of the society of that time.
Slavery was at a certain point in time, legal in United States and then with the passing of legislation later during Abraham Lincoln’s Presidency was deemed illegal. The issue is that even when slavery was legal, it was considered as unethical by some as society considered it as something wrong even when it was legal. Therefore, we can say that ethics is a far greater concept than legality. It has something to do with the basic idea of right and wrong that becomes ingrained in us from childhood. Therefore, if you do a good job and your boss steals all the credit for your work then it becomes unethical behavior on his part but it may not be illegal. An issue becomes ethical in nature when it transgresses any basic norm of human existence.
The issue of ethics in the information age has acquired a different dimension altogether. With more access to information, greater connectivity and anonymity new ethical issues are coming to the fore every day. Some major ethical issues hover around the following questions:
- How much information about an individual is private and how much that is private which cannot be captured or disclosed?
- What information can be kept by organizations dealing with individuals?
- How much right does an individual have over his/her own information?
- Who can access and who cannot access information?
Most cases of ethical violation in the information society occur due to disclosure of private information. This brings us to the interesting topic of privacy. Let us delve into the issue a little deeper. Is information about a suspected terrorist private or the act that he commits private? Probably not on the other hand if we are asked if information about a dowry victim is private, we will all probably agree that it is. Thus, we see that privacy assumes different degree of severity. In the first case, one can argue that if information about a suspected terrorist is not made public, then the terrorist will not get caught, and will cause more destruction. Thus, the well-being of a majority is at stake if the privacy of information of the terrorist is to be considered. Hence, it may be argued by some that disclosure of such private information as how he looks and what his height is may be considered fine but the same cannot be said for the latter case about the dowry victim. Thus, we see that ethics, privacy and other such related issues have to be considered carefully.
However, the following may be considered ethical issues in information society:
- Disclosing another individual’s personal details to others. This is a serious ethical issue. Sometimes when the disclosure is of a very private nature this can even become a legal issue.
- Cyber stalking is when an individual is always stalked in cyberspace resulting in violation of an individual’s privacy and creating a fear in the mind of the stalked. This on a small scale is an ethical issue but may become a legal issue if the stalking becomes serious.
- Disclosure of trusted content is also another ethical issue. If an individual is in the possession of some trusted content and he shares it with others then that becomes an ethical issue.
- Distribution of pornographic material with open access is another ethical issue and needs to be controlled.
- Plagiarism is becoming very rampant as content in soft form can just be copied and pasted from other files and claimed as one’s own. On a small scale this is an ethical issue but when the plagiarism is intentional and on a large scale then this becomes a violation of copyright which is a legal issue.
- Sending SPAM is also another ethical issue which creates a lot of problems for ordinary users of information systems
Ethics in information society is a very delicate issue and changes with time. At one point of time, stealing of password was an ethical issue. Today it is a crime and has become a legal issue. Such changes in legal and ethical points of view occur with change in legislation and with changes in the norms of society.