If a system does not employ some protocol that ensures deadlock freedom, then a detection and recovery scheme must be used. An algorithm that examines the state of the system is invoked periodically to determine whether a deadlock has occurred. If one has, then the system must attempt to recover from the deadlock. To do so, the system must.
• Maintain information about the current allocation of data items to transactions.
• Provide an algorithm that to determine whether the system has entered a deadlock state.
• Recover from the deadlock when the detection algorithm determines that a deadlock exists.
We’ll be covering the following topics in this tutorial:
Deadlock Detection
A simple way to detect a state of deadlock is with the help of wait-for graph. This graph is constructed and maintained by the system. One node is created in the wait-for graph for each transaction that is currently executing. Whenever a transaction Ti is waiting to lock an item X that is currently locked by a transaction Tj, a directed edge (Ti → Tj) is created in the wait-for graph. When Tj releases the lock(s) on the items that Ti was waiting for, the directed edge is dropped from the wait-for graph. We have a state of deadlock if and only if the wait-for graph has a cycle. Then each transaction involved in the cycle is said to be deadlocked. To detect deadlocks, the system needs to maintain the wait for graph, and periodically to invoke an algorithm that searches for a cycle in the graph.
To illustrate these concepts, consider the following wait-for graph in figure. Here:
Transaction T25 is waiting for transactions T26 and T27.
Transactions T27 is waiting for transaction T26.
Transaction T26 is waiting for transaction T28.
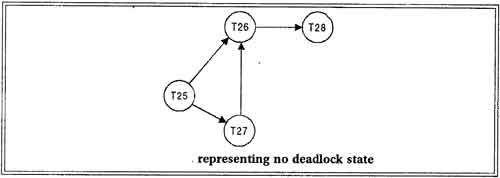
This wait-for graph has no cycle, so there is no deadlock state.
Suppose now that transaction T28 is requesting an item held by T27. Then the edge T28→T27 is added to the wait -for graph, resulting in a new system state as shown in figure.
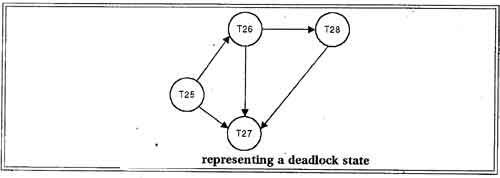
This time the graph contains the cycle.
T26→T28→T27→T26
It means that transactions T26, T27 and T28 are all deadlocked.
Invoking the deadlock detection algorithm
The invoking of deadlock detection algorithm depends on two factors:
• How often does a deadlock occur?
• How many transactions will be affected by the deadlock?
If deadlocks occur frequently, then the detection algorithm should be invoked more frequently than usual. Data items allocated to deadlocked transactions will be unavailable to other transactions until the deadlock can be broken. In the worst case, we would invoke the detection algorithm every time a request for allocation could not be granted immediately.
Recovery from Deadlock
When a detection algorithm determines that a deadlock exists, the system must recover from the deadlock. The most common solution is to roll back one or more transactions to break the deadlock. Choosing which transaction to abort is known as Victim Selection.
Choice of Deadlock victim
In below wait-for graph transactions T26, T28 and T27 are deadlocked. In order to remove deadlock one of the transaction out of these three transactions must be roll backed.
We should roll back those transactions that will incur the minimum cost. When a deadlock is detected, the choice of which transaction to abort can be made using following criteria:
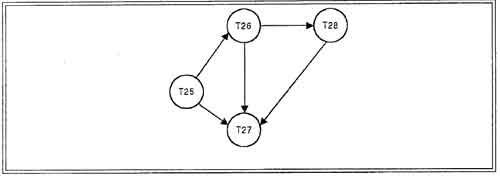 • The transaction which have the fewest locks
• The transaction which have the fewest locks
• The transaction that has done the least work
• The transaction that is farthest from completion
Rollback
Once we have decided that a particular transaction must be rolled back, we must determine how far this transaction should be rolled back. The simplest solution is a total rollback; Abort the transaction and then restart it. However it is more effective to roll back the transaction only as far as necessary to break the deadlock. But this method requires the system to maintain additional information about the state of all the running system.
Problem of Starvation
In a system where the selection of victims is based primarily on cost factors, it may happen that the same transaction is always picked as a victim. As a result this transaction never completes can be picked as a victim only a (small) finite number of times. The most common solution is to include the number of rollbacks in the cost factor.
Detection versus Prevention
In prevention-based schemes, the abort mechanism is used preemptively in order to avoid deadlocks. On the other hand in detection-based schemes, the transactions in a deadlock cycle hold locks that prevent other transactions from making progress. System put is reduced in case of detection because many transactions may be blocked, waiting to obtain locks currently held by deadlocked transactions.
This is the fundamental trade-off between these prevention and detection approaches to deadlocks: loss of work due to preemptive aborts versus loss of work due to blocked transactions in a deadlock cycle. We can increase the frequency with which we check for deadlock cycles, and thereby reduce the amount of work lost due to blocked transactions, but this entails a corresponding increase in the cost of the deadlock detection mechanism.
Deadlock detection is preferable, if different transactions rarely access the same items t the same time. This can happen if the transactions are short and each transaction locks only few items or if the transaction load is light.
On the other hand, if transactions are long and each transaction uses many items, or if the transaction load is quite heavy, it may advantageous to use deadlock prevention scheme.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular