Any access to the stored data is done by the data manager. A user’s request for data is-received by the data manager, which detern1ines the physical record required. The decision as 10 which physical record is needed may require some preliminary consultation of the database and/or the data dictionary prior to the access of the actual data itself.
The data manager sends the request for a specific physical record to the file manager. The file manager decides which physical block of secondary storage devices contains the required record and sends the request for the appropriate block to the disk manager. A block is a unit of physical input/output operations between primary and secondary storage. The disk manager retrieves the block and sends it to the file manager, which sends the required record to the data manager.
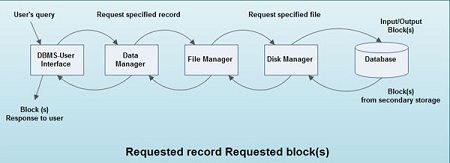
What happens when user issues a request to DBMS?
The database management system is a bridge between the application program, (that determines what data are needed and how they are processed), and the operating system of the computer, which is responsible for placing data on the magnetic storage devices.
To retrieve data from the database, the following operations are performed internally:
• A user issues an access request, using some application program or data manipulation language.
• The application program determines what data are needed and communicates the need to the database management system.
• The DBMS intercepts the request and interprets it .
• . The DBMS inspects, in turn, the external schema, the external/conceptual mapping, the conceptual schema, the conceptually internal mapping, and storage structure definition.
• The data base management system instructs the operating system to locate and retrieve the data from the specific location on the magnetic disk (or whatever device it is stored on).
• A copy of the data is given to the application program for processing.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular