Definition: Asynchronous Transfer Mode (ATM) also called cell relay (transferring data in cells of a fixed size) that is operates at the data link layer (Layer 2) of OSI Model over fiber or twisted-pair cable, a high-speed switched network technology based on ITU-T Broadband Integrated Services Digital Network (B-ISDN) standard, developed by the telecommunications industry to implement the next generation network. ATM was designed for use in WANs such as the public telephone system and corporate data networks, though it has also been applied to create super-fast LANs.
ATM can carry all kinds of traffic: voice, video and data simultaneously at speeds up to 155 megabits per second. It Convert voice, video data to packets and passing large packet data through the same medium. ATM is differing from TCP/IP because it use fixed channel routing protocol routes between two end points. A real-time low-latency application such as VoIP and video takes precedence on an ATM network.
We’ll be covering the following topics in this tutorial:
What is Asynchronous Transfer Mode (ATM)?
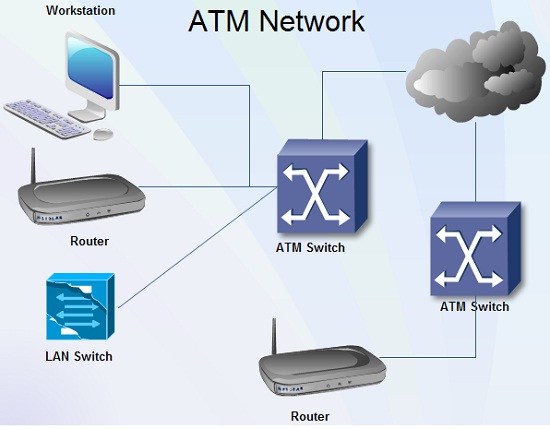
ATM is a dedicated connection-oriented switched data transfer technology, in which switches create a virtual connection or virtual circuit between the sender and receiver of a call that permanent or switched for the duration of the call. It is a small-packet switched system or similar to circuit-switched network, which breaks down messages into very small, fixed length packets called cells generally organizes digital data into 53 bytes in length (48 bytes of data plus a 5-byte header). 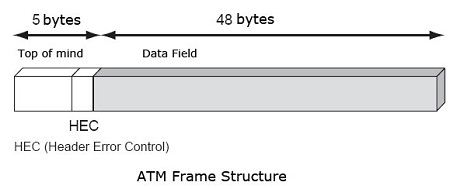
Using a fixed packet size (something that differentiates it from X.25 and the frame relay) increases the speed of data throughput since switching, and routing equipment can drive perfectly defined cells faster. ATM can conduct data at a theoretical speed of up to 2.4 Gbps, but it usually reaches speeds between 45 and 622 Mbps. The 622 Mbps are achieved, above all, in high-speed physical environments, such as ONET (synchronous optical network or synchronous optical network, a fiber-optic network developed by Bell Communications Research that provides high speeds for the transmission of voice, data, and images).
It is a connection-oriented technology (it means that you need to establish a connection between two points before making any data transfer). Once the connection is established, the cells are auto-routed because each of them contains a header that identifies the connection of the cell to which they belong.
ATM is transparent to any protocol. The ATM node passes the load of each cell without being read at the binary level. ATM uses the concept of error control and flows between endpoints (this means that the network itself does not check the data load for errors and leaves it to the final terminal device) in contrast to a conventional switched packet network that uses an error control and internal flow.
To adapt the link speed to that of the connected devices, unassigned cells inserted.
It is designed to handle the following types of traffic:
• Class A. Constant, connection-oriented transmission speed, synchronous traffic (for example, voice or video without compression).
• Class B. Variable transmission speed, connection-oriented, synchronous traffic (compressed voice and video).
• Class C. Variable transmission speed, connection-oriented, asynchronous traffic (X.25, Frame Relay, etc.).
• Class D. Offline packet information (LAN traffic, SMDS, etc.).
An ATM header can have User-Network Interface (UNI) and Network-Node Interface (NNI) two formats.
• User-Network Interface (UNI) used for communication between end systems.
• Network-Node Interface (NNI) used for communication between switches.
Two type of connections are supported by ATM (Asynchronous Transfer Mode)
Point-to-point connections: It connects either unidirectional or bi-directional two end-systems.
Point-to-multipoint connections: It connects one unidirectional ATM to number of destination ATM.
It is different in packet sizes from Ethernet data or frames. ATM is a core protocol for SONET that is the backbone of ISDN. The advantage conferred by such small cells is that they can be switched entirely in hardware, using custom chips, which makes ATM switches very fast (and potentially very cheap).
The asynchronous part of the name refers to the fact that although ATM transmits a continuous stream of cells over a physical medium using digital signal technology, some cells may be left empty if no data is ready for them so that precise timings are not relevant. Every cell is encoding data with asynchronous time-division multiplexing (TDM) and it queued before being multiplexed over the transmission path.
Every cell are encodes data and processed within their time slot allocated to it. When cell time slot allocated is finished, the next cell starts same procedure. That’s why it’s called asynchronous time-division multiplexing (TDM);
This is ATM’s greatest strength, as it enables flexible management of the quality of service (QoS) so; an operator can offer different guaranteed service levels (at different prices) to different customers even over the same line. This ability will enable companies to rent virtual private networks based on ATM that behave like private leased lines but in reality share lines with other users.
Available ATM service: Generally four data bit rates are available for ATM services: constant bit rate (CBR), variable bit rate (VBR), available bit rate (ABR) and unspecified bit rate (UBR).
ATM features
1. It is a connection-oriented protocol: it means that a connection must establish between the transmitting and receiving computers before data transfer. Each intermediate switching point must be identified and informed of the existence of the connection. Each package is rerouted independently and, therefore, must enter the full address of its final destination. It guaranteed that all cells arrive at their destination in the same order in which they left; however, it not guaranteed that all the cells arrive, in situations of severe congestion it considered acceptable that there is a minimal loss of cells (for example one in 1012).
2. It is full-duplex: it allows the transmission through one pair of threads and the reception through another pair of threads simultaneously, which provides almost complete use of both pairs and high constant data rates. To support the full-duplex mode of operation, ATM doubles the effective bandwidth of the usual half-duplex transmission used by most network protocols.
3. It is a point to point: as mentioned before, ATM networks must establish a connection between the sender and receiver before the transmission of the cell. This connection between the two stations is the only concern of the ATM switch. Unlike a router (router), an ATM switch does not attempt to define a unique connection within the context of all possible network connections. Instead, the ATM switch selects the route between the sending station and the receiving station and then informs the intermediate switches along this route, to ensure that the resources necessary to transmit the cell through of the network are assigned. Once a transmission route has established for the cell, the ATM switch assigns a connection number to each of the existing point-to-point links along this route. The connection numbers are chosen independently for each of the point-to-point links in the transmission path. A path can form by any number of these links, the links linked by switches. This means that a cell potentially carries a different connection number on each different link in the connection path. A switch modifies the connection numbers of each cell as it transfers the cell from one link to another. This change of the connection numbers in the union of two links implies that the connection number fields only need to be large enough to distinguish the connections maintained by a single link. This point-to-point orientation of the ATM connection and the modification of the connection numbers in each switch jump allow ATM to use reduced connection numbers instead of the large addresses needed in most protocols. It makes ATM more efficient because small connection numbers preserve cell space and, therefore, bandwidth and also faster because it reduces the search in switch tables.
4. Dedicated bandwidth: the efficient use of bandwidth is not a problem that only concerns ATM technology. Different types of traffic require different behaviour regarding the delay, delay variation and loss characteristics. ATM provides different service qualities to accommodate those differences. It also assigns bandwidth to each of the active stations. The station requests the appropriate amount of bandwidth for each connection, and the network automatically assigns this bandwidth to the user. Bandwidth not dedicated per user. It shared with other users, but the network ensures the level of service requested. The network can do this because it controls the number of simultaneous conversations on the network. To access the network, the station requests a virtual circuit between the transmitter and receiver ends. During the establishment of the signal, the receiving station can request the quality of service it needs to adapt to the transmission requirements, and ATM switches guarantee the request if there are sufficient network resources available. The guaranteed service level of cell-based switching access is particularly useful for transporting real-time interactive communications such as voice and video. ATM uses a protocol called User-to-Network Interface (UNI) to establish the bandwidth levels dedicated to stations and applications.
5. ATM is asynchronous: in contrast to T1, there is no requirement that cells from different sources alternate rigidly. Random orders and even flow gaps are permissible.
6. ATM does not specify the medium: it is possible to use fibre-like cables, with point-to-point and full-duplex connections. The main speed is 155.52 Mbps; the alternative is 622.08 Mbps (compatible with SONET).
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular