A Wi-Fi network is made with many amenities, such as access points, antennas, bridges, controllers, etc. In this section, we will make an overview of the equipment in order to provide some features.
This equipment is usually quite heterogeneous, an IETF working group focused on how to make corporate networks using multiple suppliers. This group, called CAPWAP (Control and Provisioning of Wireless Access Point), proposes to classify wireless architectures in three architectures:
• Standalone WLAN (Autonomous WLAN Architecture)
• Centralized WLAN (Centralized WLAN Architecture)
• Distributed WLAN (Distributed WLAN Architecture)
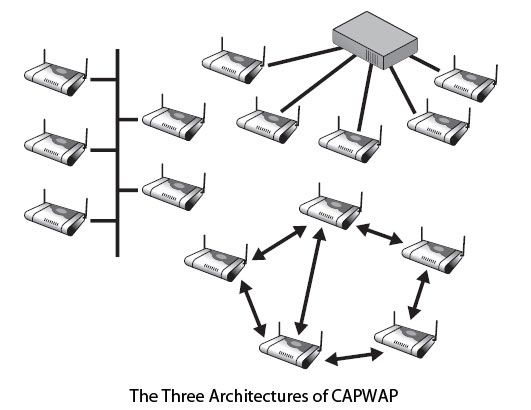
These architectures are illustrated in Figure. The first on the left in the figure corresponds to the access points “heavy”, which are autonomous and are managed by themselves.
The second (top right), used in corporate networks, uses a controller. The controller allows to centrally managing a large number of access points. Most functions are grouped in the controller. In this case, the access points are alleviated. We talk about access points “light”. The latter architecture (bottom) is that of a mesh network. It’s distributed architecture.
We’ll be covering the following topics in this tutorial:
Access points Wi-Fi
Unlike Wi-Fi cards, access points are available in different formats. The choice of an access point is thus made according to the proposed functionality.
The primary function of the access point is to allow communications within the coverage area. The proposed features are limited and depend on the context of use of the access point home, in business or in a hotspot.
Some manufacturers offer so-called access point software. These are nothing but stations generally stationary computers, equipped with Wi-Fi cards in which software is installed and turn them into access points. Free software, such as Host AP, to configure wireless station access point.
The domestic access points
The role of a home access point is to enable the wireless connection to the Internet. If you wish to connect multiple stations, the access point must allow tethering.
This type of access point incorporates the following mechanisms:
• ADSL modem / cable. Integrating an ADSL / cable modem is increasingly common. It avoids the purchase of such equipment from the ISP, if it does not give it for free.
• NAT (Network Address Translation). This mechanism enables the sharing of the Internet connection.
• DHCP (Dynamic Host Configuration Protocol). This mechanism is based on client-server architecture to enable automatic configuration of wireless terminals network settings. DHCP is totally transparent to the user, but first requires that stations be configured to allow this automatic setting.
• Firewall. Because the Internet connection is shared, it is necessary to apply a firewall to prevent any attempt of attack (viruses, Trojan horses or worms) by blocking the use of certain applications that provide door entry to these attacks.
Most access points integrate an Ethernet switch ports 1-5 for sharing the Internet connection for both the Wi-Fi network for Ethernet.
In the case where the coverage area of the access point does not allow the connection of all the stations to the network, a change of antenna is needed. The access points for individuals have either an antenna connector, if the antenna of the access point is internal, or the ability to change the antenna or external source antennas. Before any change of antenna, we obviously check the type of connector proposed.
While security is an important element to consider, it is generally satisfied, as part of a home Wi-Fi network to use the basic mechanisms of Wi-Fi:
• Non-Broadcast SSID (Secure Set Identifier).
• ACL (Access Control List), which defines terminals, allowed connecting.
• WEP (Wired Equivalent Privacy), preferably of 128 bits, which provides authentication and encryption of communications by means of a user-defined key.
These mechanisms are not flawless, but it is considered that they are sufficient to secure the individual connections. The addition of specific security systems that would lead to additional network equipment, which would complicate the configuration and generate a significant cost.
Enterprise access points
Unlike the access points for individuals, corporate access points usually have the sharing features of the internet access router, NAT and DHCP server, the latter also being used in the Ethernet network.
In one company, the access point must facilitate configuration, scalability, installation and connections with enhanced security.
The proposed features are:
• Configuring the Access Point. Optimization of Wi-Fi network is an essential criterion for the network administrator. This optimization primarily involves the configuration of different parameters related to the radio part or 802.11. For example, limiting the transmission power of the access point or the authorized debits are often quite decisive criteria.
• Scalability. To avoid changing the entire installed base of equipment, it is necessary that the access point allows the addition of modules turning it into multi-standard access point.
• PoE (Power over Ethernet). When installing an access point, it must be connected to the corporate network via an Ethernet cable and powered by an electrical outlet. The PoE performs both functions in one, providing power to all equipment through the Ethernet cable.
• Log of network events. It is important for the network administrator to know what is happening on its network to protect against any type of attack. The access point should therefore allow memory storage of all connections, both successful as unsuccessful.
• Handover. The handover, or intercellular movement, keeps the transmission in progress when moving from one cell to another, ie from one access point to another. This feature is not present in the 802.11 standard, it is defined such owner by the manufacturers. If the company wants to be equipped with a wireless telephony system, this mechanism is necessary under penalty of having a break in the conversation during a handover phase.
• Security. Given the Wi-Fi security vulnerabilities, it is necessary that the access point incorporates all available safety systems, such as 802.1x (EAP-TLS, EAP-TTLS or PEAP), 802.11i, HTTPS and especially VPN (Virtual Private Network) or virtual private network.
• VLAN (Virtual Local Area Network). This mechanism lets you create multiple virtual networks within a physical network and allocate specific configurations created for each virtual network.
When the coverage area does not allow the connection of all stations in a particular place of business or the access point to be used to establish a link directive, it must allow the addition of additional antennas, which is usually the case.
If the company has more than a dozen access points, it is helpful to have a software or hardware solution that automatically sets all access points.
The access points to hotspot
The role of a hotspot is to offer seamless connections for customers. The Wi-Fi network must accept all connections from many and varied devices. Hotspots are usually equipped with 802.11b or 802.11g, 802.11a very rarely.
The characteristics of these access points are similar to those access points businesses, such as configuring or scalability because the hotspots must support different standards.
Transparent communication requires the following two mechanisms:
• Evolution of network settings. Configuring network parameters of a station can be static or dynamic. If it is dynamic, use the DHCP settings allocate these parameters dynamically. If these parameters are static, IP address of the station and that of the network do not match, and it is impossible for the station to communicate with the hotspot network. This mechanism virtually allocated to the station address of the hotspot network without physically it changes its IP address, allowing the station to communicate with the hotspot network.
• SMTP Diversion. Unlike the network settings of a station, POP and SMTP mail settings are configured manually by the user or administrator of the machine. Or SMTP servers being adapted to an ISP or company, when moving from one area to another, it is not possible to send messages. The SMTP redirection enables transparent, the sending of emails without the user having to change the configuration of the email client. This is the access point that is responsible for redirecting the mail by modifying the SMTP server. Given that email is the most used application in a hotspot, with 80% of traffic, it is essential for a hotspot to implement this feature.
The number of access points installed in a hotspot such as an airport or a railway station being about a hundred, it is essential to have software or hardware solution for configuring all access points simultaneously and not sequentially.
The wireless controllers
Supervisors play an important role in enterprise networks. They may be linked to an OEM or independent. In the former case, the features are complementary to those in the access point and those in the controller. The major drawback is having to stay in the lap of the OEM. Open controllers allow connection of most lightweight access points and are much more open.
The main functions of a controller are:
• Manage the transmit power of the access points to enable them decrease or dependent increase in electromagnetic field or failures of others access points.
• Manage the choice of frequencies to suit the frequency plan at access points.
• Manage security problems, by introducing an authentication server in the controller.
• Manage intercellular passage problems (handover) between different cells, even if they are not from the same technology.
• Implement nomadic management software for assigning affected users the access permissions and the services to which they are entitled.
To go a little further in this new generation of management of nomadism, take the example of UCOPIA controller that is shown in Figure.
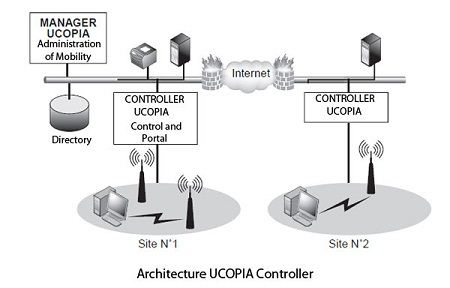
All traffic from the wireless user is redirected to the UCOPIA controller, which is a logical failure (or physical) access points between a park and the wired network. The controller filters the Wi-Fi stream to apply the security policies defined and nomadism with UCOPIA Manager. The controller complies with the 802.11i standard. The authentication protocol between the wireless user stations and UCOPIA controller is based on 802.1x / EAP or HTTPS. Flows are encrypted or in TKIP or AES. In addition, an IPsec-based VPN can be established between the wireless client and the controller. The RADIUS authentication server and the Manager UCOPIA interact with LDAP directories or through the LDAPS secure protocol.
The UCOPIA solution allows very precise management of the addressing mechanism on the wireless network, depending on their profile and the controller configuration. One possibility is to direct their traffic in different VLANs on the wired network controller output. Companies often architecting their network VLAN to isolate users, it is important to ensure consistency between the wireless and wired infrastructures and continue to benefit from the network isolation mechanisms on the wired network. The Wi-Fi side, the network organization can also benefit from structured VLANs by encapsulating the SSIDandVLANbycombiningtheirdifferentiatedaddress ranges.
The solution in environment UCOPIA multisided can be deployed with one or more UCOPIA controllers. The controllers can be centralized on a site or distributed across different sites. Regardless of the architecture of controllers directories can also be centralized or replicated to each site. For sites distant including few access points and / or connected to the main site by a level 3 network connection, UCOPIA offers a bridge for establishing a tunnel emulating level 2 link between the remote site and the main site. Thus, the remote terminals are managed centrally without local controller. UCOPIA The solution includes all modules necessary for its functioning, which enables it to be proposed in a mode “turnkey” very simple to implement. This packaging is ideal for small businesses or remote branches of a large company, having few needs and means of integration. Conversely, large enterprises with complex network infrastructures, wish to reuse solutions already deployed in terms of security or network organization.
With its open and modular architecture, UCOPIA can integrate seamlessly into existing network architectures and interoperate with the tools in place (LDAP, RADIUS server, VPN, DHCP, PKI, etc.).
The Wi-Fi bridges
As an Ethernet bridge, wireless bridge function is to extend the network. In the case of Wi-Fi, we extend the Ethernet network on the Wi-Fi network and vice versa.
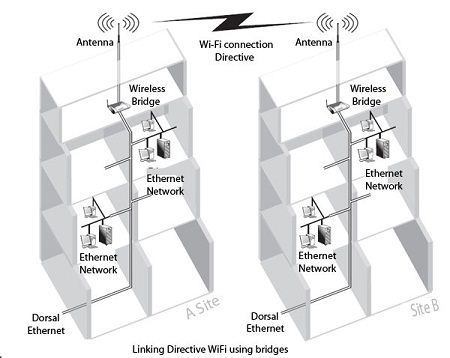
One of the main uses of wireless bridges is to connect between buildings through wireless line basis. For this, the bridge should allow the addition of a specific antenna and the networks have all the necessary security mechanisms.
Figure shows a Directive connection using Wi-Fi bridges.
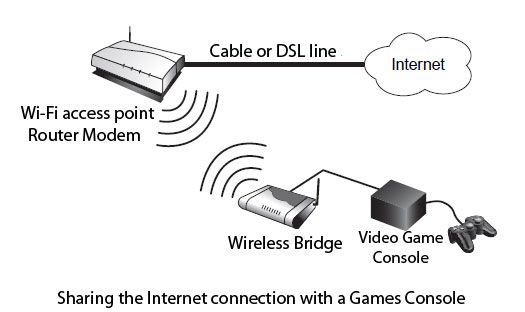
Another use of the bridges is to offer, through the access point to which it is connected, Internet access to a games console. All the latest generation of game consoles (PlayStation 2, Xbox and GameCube) have indeed an Ethernet network connection. Through a particular module, simply connect the wireless bridge to the console via an Ethernet cable to benefit from the connection.
This operation is illustrated in Figure.
The Wi-Fi antennas
In a Wi-Fi network, the signal transmitted between stations or between a station and an access point may be subject to interference from obstructions to cross or equipment transmitting in the same frequency band. The range of the radio signal is a function of both of these interferences, the obstacles in the environment and the transmission power.
If the range of the Wi-Fi network is not suitable for the intended use, equipment such as amplifiers allow to increase the coverage area by increasing the power of the transmitted signal, knowing that this power must not exceed the set value by the local regulator (ARCEP in France).
In practice, each wireless card is equipped with an internal omni-directional antenna, which can be mobile if the resort itself is mobile. If a station is hidden by obstacles such as walls, furniture, people, etc., or it is some distance from the access point, it may be that it can access the network.
In some cases, even if the station and the card are placed in an enclosed area, behind a desk, for example, the antenna can operate correctly. Indeed, WiFi retrieves the transmissions from the reflections of radio waves in the environment. Depending on the environment, these reflections may be more or less strong, but it allows some stations to operate despite their spatial constraints. In cases where the card does not work very well, if at all, adding a directional antenna is required.
Figure shows a Wi-Fi network with antennas.
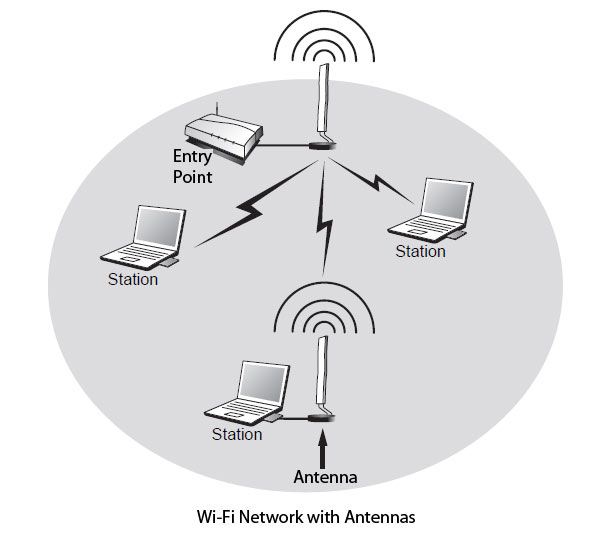
An antenna can be used by both stations located at the network edge, or where the signal is weaker than the access point or bridge to extend the network coverage area. The role of the antenna is not to amplify the signal, as would an amplifier, but to improve the reception and transmission of signals. The use of an antenna can also be used to create links between directives buildings at distances up to 30 km.
To improve the coverage of a Wi-Fi network, an omni directional antenna is Recommended. A station can be satisfied with a directional antenna, or sector. In the case of wireless links between buildings, the choice is limited to directional antennas. This concept is related to the directivity gain of the antenna. The higher the gain, the greater the directivity is stronger and the coverage area is limited.
This is expressed by the directivity gain of the antenna, which is based on an antenna that evenly radiates, that is to say 360 °, and would like coverage area a perfect sphere. This type of antenna exists only in theory, because of the physical limitations of electromagnetic waves.
The antenna gain is expressed in decibels isotropic (dBi). This gain is equivalent to a power, wherein the following formulas:
P = 10 G/10 Where G = 10logP
Where G is the gain (in dBm or dBi) and P the power (in mW).
The gain and power depend on the antenna and its directivity. The French laws restrict power to a power EIRP (effective isotropic radiated power effective).
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular