What is FTP? One of the most popular uses of the Internet is to download files – that is, transfer files from a computer on the Internet to your computer. Many thousands of files are downloaded every day from the Internet. Most of these files are downloaded using the Internet’s File Transfer Protocol, commonly referred to as FTP. This protocol can also be used to upload files from your computer to another computer on the Internet.
We’ll be covering the following topics in this tutorial:
FTP (File Transfer Protocol)
File Transfer Protocol is a standard network protocol used to exchange and manipulate files over a TCP/IP-based network, such as the Internet. FTP is built on client-server architecture and utilizes separate control and data connections between the client and server applications. FTP is used with user-based password authentication or with anonymous user access. Applications were originally interactive command-line tools with standardized command syntax, but graphical user interfaces have been developed for all desktop operating systems in use today. The Trivial File Transfer Protocol (TFTP) is a similar, but simplified, not interoperable, and unauthenticated version of FTP.
Numerous FTP servers all over the world allow users anywhere on the Internet to log in and down-load files placed on them. The main competitor for FTP is HTTP (Hyper Text Transfer Protocol) and the day is not very far when sites would run HTTP servers instead of the FTP servers. It is so because HTTP servers can do whatever FTP server can do and do it more efficiently.
As the Web gains popularity, downloading software is becoming even easier. You can use your Web browser and click on links to files; behind the scenes, FTP is often still downloading the files.
One problem with downloading files over the Internet is that some files are so large that it can take a tremendous amount of time to download them. As a way to speed up file transfers and save space on the FTP server, files are commonly compressed. Many different methods are used to compress files. After the files have been downloaded, you will need to run the decompression software such as PK UNZIP to decompress the files to use them.
Once you have the compressed file such as data. zip, you will need to unzip or decompress it to get to the setup file and install the program. You can use the WinZip file to uncompress this file.
Shareware: Shareware is the software that is distributed for free (sometimes in a limited or list format) on a trial basis. If you like the software and want to continue to use it beyond its trial period, it is your responsibility to register and pay for it.
Software distributed absolutely free is called freeware. Programmers who make freeware either derive personal satisfaction from the adoption and use of their handiwork or benefit financially from the reputation that accrues to the developer of a popular program.
The web site address for good shareware is given below
http://hyperarchive.lcs.mit.edu
Features of FTP
The basic features of FTP are:
1. Data representation
• FTP handles three types of data representations-ASCII (7 bit), EBCDIC (8-bit) and 8-binary data.
• The ASCII file is the default format for transferring text files
• Each character is encoded using 7-bit ASCII. The sender transforms the file from its own representation into ASCII characters and the receiver transforms the ASCII character to its own representation.
• The image file is the default format for transferring binary files. The file is sent as continuous streams of bits without any interpretation or encoding.
2. File organization and Data structures
• FTP supports both unstructured and structured file.
• An unstructured file contains string of bytes and is enl-marked by EOF (End of file). The data structure that corresponds to such a file is called file structure.
• A structured file contains a list of records and each record is delimited by EDR (End of Record). The data structure of such file is called record structure i.e. file is divided into records.
• Another structured file contains pages, with each page having a page number and a page header. The pages can be stored and accessed randomly or sequentially. The corresponding data structure is called page structure i.e. file is divided into pages.
3. Transmission modes
• FTP can transfer a file by using one of the following three modes:
Stream mode
• It is the default mode.
• File is transmitted as continuous stream of bytes to TCP.
• TCP is responsible for chopping data into segments of appropriate size.
• If data is simply a stream of bytes (file structure), no end-of-file is needed. EOF in this case is the closing of the data connection by the sender.
• If data is divided into records (record structure), each record has a I-byte EOR (End-of-Record) character and the end of the file has a I-byte EOF (End-of-file) character.
Block mode
• Data is delivered from FTP to TCP in blocks.
• Each block is preceded by 3 bytes header.
• The first byte is called the block descriptor.
• The second and third byte defines the size of the block in bytes.
Compressed mode
• Data is usually compressed if the file to be transmitted is very big.
• The compression method normally used in Run-length encoding.
• In a text file, usually spaces (blanks) are removed.
• In a binary file, null characters are compressed.
4. Error control
• Since TCP is used for data transfer no additional error recovery mechanism is required.
5. Access control
• File access protection is done using login procedure with login name and password.
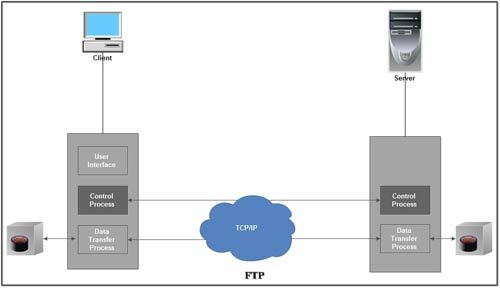
FTP operation
• FTP uses client/server model for communication.
• Two TCP connections are used for file transfer.
• On one connection control signals (commands and responses) are exchanged and the other connection is used for actual data transfer. These two connections are called control connection and data connection respectively.
Control Connection
The Control connection has following features:
1. It is used to transfer control signals (commands and responses) between the client and server.
2. This connection is used by the control process of client and server. The control process is called Protocol Interpreter (PI).
3. The TCP connection for control signal uses well-known FTP server port 21.
4. This control connection remains connected during the entire interactive FTP session.
5. The control connection uses very simple rules of communication. We need to transfer only a line of command or a line of response at a time.
6. The two control processes (client & server) or PI communicates using NVT syntax.
7. The PIs are responsible for translating the local code or syntax. (e.g. DOS or UNIX) into NVT syntax and vice-vers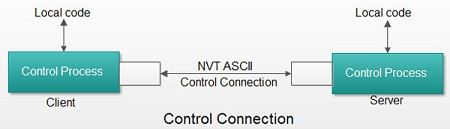
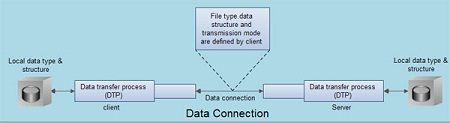
Data Connection
The Data connection has following features:
1. Data connection is used for actual data transfer.
2. This connection is established between the Data Transfer Process (DTP) of client and server
3. The server port used for data connection is Port 20.
4. The data connection is opened and then closed for each file transferred. It opens each time commands that involve transferring files are used, and it closes when the file is transferred.
5. File transfer occurs over the data connection under the control of the commands sent over the control connection.
6. During the file transfer, the client must define the type of file to be transferred, the structure of data and the transmission mode.
Thus file transfer in FTP means one of three things:
1. A file is to be copied from the server to the client. This is called retrieving a file. It is done with help of RETR command.
2. A file is to be copied from the client to the server. This is called storing a file. It is done with STOR command.
3. A list of directory or file names is to be sent from the server to the client. This is done with LLST command.
Anonymous FTP
• To Use FTP, a user needs an account (user name) and a password on the Remote server.
• Some sites have a set of files available for public access; to enable anonymous FTP.
• To access these files, a user does not need to have an account or password. Instead, the user can use Anonymous as the user name and guest as the password.
FTP Servers
Similar to the Web servers, the Internet also has the installations of FTP servers. Many organizations use FTP servers to handle the distribution of files. When a user links to download something, the link actually redirects to FTP, instead of HTTP. Some files in the FTP servers may be accessible to the general public, while others are accessible only by the user. To separate the general public from the more private users, FTP servers are divided into two parts:
Anonymous server
Non-anonymous server
1. Anonymous Server: Anonymous server is the most common use of FTP, the Internet file transfer protocol. FTP sites that allow anonymous FTP do not require a password for access. You only have to log in as anonymous and enter your e-mail address as password (for their records).
2. Non-anonymous Server: If you use a non-anonymous server, then you will log in as yourself and give your password.
FTP AUTHENTICATION: FTP authentication is very easy. To authenticate the users against an existing FTP server, edit ezproxy.usr and then write a line like this: : :ftp =ftpserv.mylib.org
After writing this line, replace “ftpserv.mylib.org” with the appropriate host name for the
FTP server. Changing this line with host name takes effect immediately, without the need to restart EZproxy. When EZproxy receives authentication requests, it will connect the user to the FTP server, and if the FTP server shows login success, then the remote user will be authenticated and allowed to proceed.
FTP CLIENTS
FTP runs on a client /server model. For using FTP you will need client software to run on your PC.
To begin an FTP session, you run the FTP client software and contact the FTP server from where you want to download files from. You can use FTP client software available in Windows 2000. The FTP client talks to an FTP server. FTP uses TCP to handle communications and creates a session between the two hosts.
The FTP daemon runs on the FTP server. This daemon handles all FTP transactions. When an FTP client contacts a server, the daemon will ask for an account number (or user name) and password. Many FTP sites allow anonymous FTP.
When you log on to the FTP server, a connection called a command link is opened between your computer and the server. This link is used for sending commands to the server from your computer, and sending messages and information back from the server to your computer.
When you want to change directories on the FTP server, your client software sends an instruction to the FTP daemon, using the command link. The daemon changes directories and then sends back a listing of files on that directory via the command link. On your client software, you will see a listing of files in the new server directory. When you want to download a file, the request is issued over the command Jink.
When you issue a command to download a file, a second connection is opened up, called the data connection or data link. This connection can be opened up in one of the following two modes:
ASCII Mode
Binary Mode
Line Mode
1. ASCII Mode: The ASCII mode is used for sending text files and alters things such as line feed and carriage returns.
2. Binary Mode: The binary mode is used for sending binary files and lets files through untouched.
3. Line Mode: Line mode FTP is used to send text files line by line or it is similar to ASCII mode but with additional features. The file is downloaded from the server to your computer via the data connection. After the file is [downloaded, the data link closes automatically. After this, the command link stays open. You can then change directories or download more files.] After you have finished the whole job, you log off command link closes. Then, you are no longer selected to the FTP server.
Connecting with FTP
Typical FTP session starts as client, when you the FTP program and connect to an FTP site, spending on the program you have, you will ? enter your login information before connect or you will be prompted to do it after you connect. If you are using a Web browser to connect to anonymous site, the browser will prompt you to connect to an FTP site; you need to know the IP of an account on the FTP server. In other Is, you need to login with a user name and password so that the server knows who you are. y accessible FTP sites expect you to use a account called anonymous. Unless you spec-, Internet Explorer assumes that you warn to con-to FTP sites as an anonymous user, and it supplies the server with the user name anonymous and a password consisting of your own e-mail address.
To connect to an FTP site do this:
1. Enter the URL of the FTP site in the Address box and click go. For example, to connect to FTP site rtfm.mit.edu/publ enters the URL as follows ftp://rtfm.mit.edu/pub/
2. The browser opens the specified sites.
3. Display the directory that contains the file you want to download.
4. Right click the file and choose copy to folder.
5. Once you have saved the file in computer’s drive, you can open it using the appropriate software, depending upon the type of file. If it is a Doc file, you can use Microsoft Word to open this file.
FTP Common commands
The basic command is:
FTP hostname: This command written at the DOS prompt and it opens an interactive FTP session. When you want to run FTP in a script, the available switches are as follows: ftp [-v] [-ell [-i] [-n] [-g] [-s:filename] [-a] [-w:windowsize] [computer] summarizes the parameters that you can enter the command.
Most of the time, you use the FTP client in interactive mode. You should be aware of several commands when you are in this mode. Table lists some of the most common valid commands for the Microsoft FTP clients.
Many of the FTP commands are similar to DOS commands. For example, rmdir is the same as rd in DOS. mkdir, mdir are both used to make directory on the remote host. The other command is help which has the same function as in DOS. The type command types the ASCII characters of the file.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular