It is a simple protocol used for opening the remote e-mail boxes. This protocol is defined in RFC 1225. Post Office Protocol version 3 (POP3) is a message access protocol that enables the client to fetch an e-mail from the remote mail server.
SMTP expects the destination host, the mail server receiving the mail, to be on-line all the time; otherwise TCP connection cannot be established. The server receives the mail on behalf of its clients.
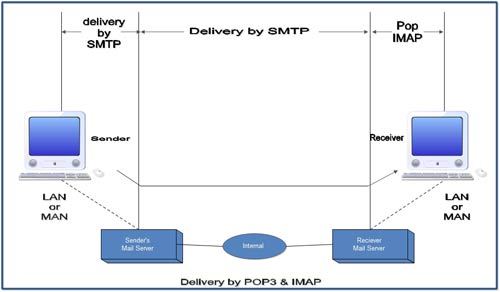
A POP3 server stores messages for each user until the user connects to download and read them using a POP3 client such as Microsoft Outlook 98, Microsoft Outlook Express, or Microsoft Mail and News.
To retrieve a message from a POP3 server, a POPS client establishes a Transmission Control Protocol (TCP) session using TCP port 110, identifies itself to the server, and then issues a series of POP3 commands:
stat: It asks the server for the number of messages waiting to be retrieved.
list: It determines the size of each message to be retrieved.
retr: It retrieves individual messages d. Quit: Ends the POP3 session.
Mail access by POP3
• The client POP3 software is installed on the receiver’s computer the server POP3 software is installed on the mail server.
• POP3 is described in RFC 1939 and it uses well-known TCP port 110.
• The communication procedure is similar to SMTP and uses ASCII characters.
• POP3 begins when user starts the mail reader.
• The mail reader calls up the ISP (or mail server) and establishes a TCP connection with the message transfer agent at port 110.
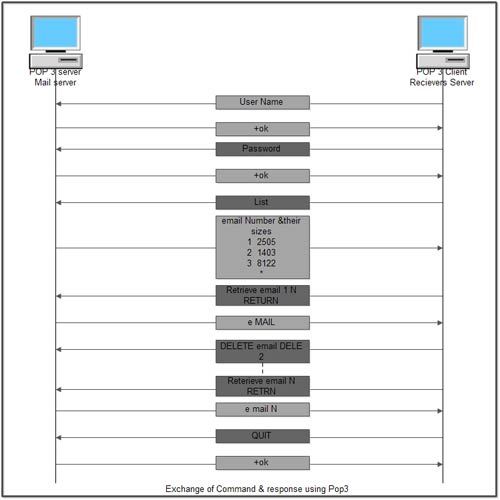
• Once the connection has been established, the PO?3 protocol goes through three states in sequence
1. Authorization
2. Transactions
3. Update
• The Authorization state deals with user log in. The client sends its user name and password.
• The transaction state deals with the user collecting the e-mails and marking them for deletion from the mailbox.
• The update state causes the e-mails to be deleted.
• Once the user has logged in, the client can send the LIST command to list the contents of its mailbox. In this case the server displays one message per line along with its length. This list ends with a period.
• The client can retrieve messages using RETR command and can also mark them for deletion with DELE.
• When all the messages have been retrieved, the client gives QUIT command to end the transaction state and enter the update state.
• When the server has deleted all the messages, it sends a reply and breaks the TCP connection.
• Although POP3 is used to download messages from the server, the SMTP client is still needed on the desktop computers to forward messages from workstation user to its SMTP mail server.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular