Another big wireless network category is ad-hoc networks, where the infrastructure is composed as resorts themselves. The latter agreed to play the role of the router to allow the passages of information from one device to another, without these terminals are connected directly.
An ad hoc network is shown in Figure.
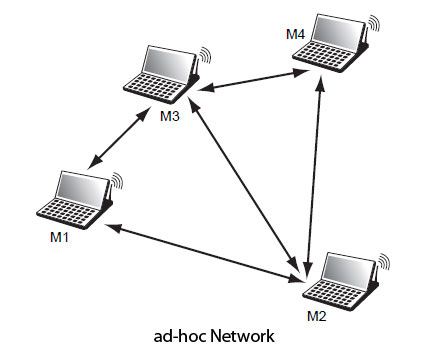
Contrary to appearances, ad-hoc networks date back several decades. They aim to achieve a communication environment that unfolds without any other infrastructure that mobile themselves. In other words, the mobile can act as a gateway for allowing a mobile communication to another. Two moving too far away from each other to directly communicate can find an intermediate wheel able to act as relays.
The main problem caused by this network comes from the definition of the network topology: how to identify the neighboring nodes and how to get from one node to another node? Two extremes can be compared. The first is that of an ad-hoc network in which all nodes can communicate with all the other involving long-range transmitters. In the second solution, instead, the radio range is as short as possible: in a communication between two nodes, it usually go through several intermediate machines. The advantage of the first solution is the transmission security, since you can go directly from the sender to the receiver, without depending on an intermediate device. Network throughput is minimal, the frequencies that can not be reused. In the second case, if a device fails or is turned off, the network can be cut into two separate subnets, without communication with each other. Obviously, in this case, the overall throughput is optimized, since there may be a high frequency reuse.
The access techniques are the same type as in mobile networks. However, the fact that all portable play the role of BSS and are themselves mobile, new properties should be made to the management of user addresses and control routing.
The solution developed for ad-hoc networks takes to the foundation IP environment. Mobile which acts as gateways – usually all mobile – implement a router in the circuits, so that the problems arising essentially return to the Internet routing problems, the mobility is managed by IP Mobile.
The benefits of ad-hoc networks are their simple extensions, physical coverage and cost. However, to benefit fully, a number of pitfalls to be overcome, such as quality of service and security, because of the mobility of nodes.
MANET (Mobile Ad-hoc Network) is the IETF working group that is concerned with the standardization of ad-hoc protocols running over IP. This group has relied on conventional Internet protocols and improved them so they can work with mobile routers.
Two major protocol families were defined: reactive protocols and proactive protocols:
• Reagents Protocols. The terminals do not maintain routing table but are concerned about it when a show is performing. In this case, it is primarily used to flood techniques to identify mobile that can participate in the transmission.
• Proactive Protocols. Mobile seeks to maintain a consistent routing table, even in the absence of communication.
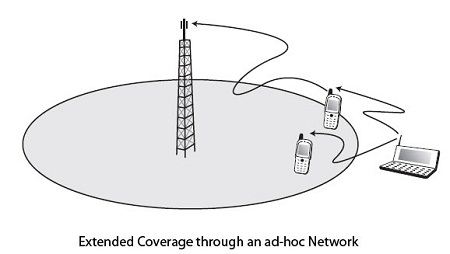
Ad hoc networks are useful in many cases. They allow to set up networks within a limited period of time, if, for example, earthquake or a meeting with a large number of participants. Another possibility is to extend access to a cell of a wireless network such as WiFi. As shown in Figure, a terminal outside of a cell can connect to another user’s machine located in the cell coverage area. The latter serves as an intermediate router to access the antenna of the cell.
The ad-hoc networks pose many problems because of the mobility of all equipment. The main one is the routing required transferring packets from one point to another point in the network. One of the objectives of MANET group is to propose a solution to this problem. For now, four proposals have emerged, two reagent types and two proactive type. Among other issues, we find the safety, quality of service and mobility management during the call.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular