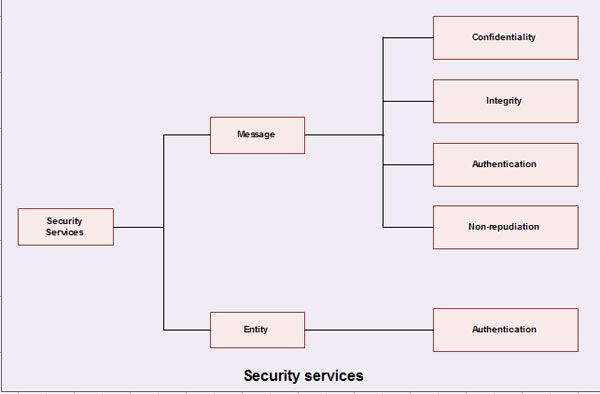
Network security can provide the following services related to a message and entity.
We’ll be covering the following topics in this tutorial:
1. Message confidentiality
• It means that the content of a message when transmitted across a network must remain confidential, i.e. only the intended receiver and no one else should be able to read the message.
• The users; therefore, want to encrypt the message they send so that an eavesdropper on the network will not be able to read the contents of the message.
2. Message Integrity
• It means the data must reach the destination without any adulteration i.e. exactly as it was sent.
• There must be no changes during transmission, neither accidentally nor maliciously.
• Integrity of a message is ensured by attaching a checksum to the message.
• The algorithm for generating the checksum ensures that an intruder cannot alter the checksum or the message.
3. Message Authentication
• In message authentication the receiver needs to be .sure of the sender’s identity i.e. the receiver has to make sure that the actual sender is the same as claimed to be.
• There are different methods to check the genuineness of the sender :
1. The two parties share a common secret code word. A party is required to show the secret code word to the other for authentication.
2. Authentication can be done by sending digital signature.
3. A trusted third party verifies the authenticity. One such way is to use digital certificates issued by a recognized certification authority.
4. Message non-reproduction
• Non-repudiation means that a sender must not be able to deny sending a message that it actually sent.
• The burden of proof falls on the receiver.
• Non-reproduction is not only in respect of the ownership of the message; the receiver must prove that the contents of the message are also the same as the sender sent.
• Non-repudiation is achieved by authentication and integrity mechanisms.
5. Entity Authentication
• In entity authentication (or user identification) the entity or user is verified prior to access to the system resources .
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular