• Message authentication ensures that the message has been sent by a genuine identity and not by an imposter.
• The service used to provide message authentication is a Message Authentication Code (MAC).
• A MAC uses a keyed hash function that includes the symmetric key between the sender and receiver when creating the digest.
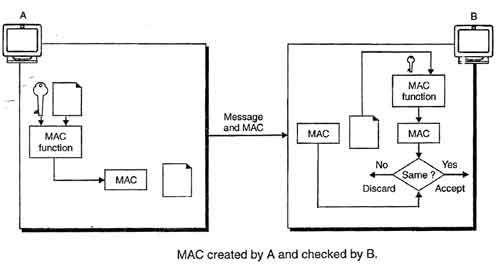
• Figure shows how a sender A uses a keyed hash function to authenticate his message and how the receiver B can verify the authenticity of the message.
• This system makes use of a symmetric key shared by A and B.
• A, using this symmetric key and a keyed hash function, generates a MAC.
• A then sends this MAC along with the original message to B.
• B receives the message and the MAC and separates the message from the MAC.
• B then applies the same keyed hash function to the message using the same symmetric key to get a fresh MAC.
• B then compares the MAC sent by A with the newly generated MAC.
• If the two MACs are identical, it shows that the message has not been modified and the sender of the message is definitely A.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular