The frame level (layer 2) is to render a service to the next level just. This service is a transport node to node packet. Specifically, its role is to transport a package of three or message fragment layer of layer 4 from one node to another node. For this, the frame level asks his turn at just below, the physical level, a service of conveying the bits of the frame from one node to another node. This section provides the features necessary to achieve all these actions.
We’ll be covering the following topics in this tutorial:
The functionality of the frame level
The specificity of the frame level is to transmit information as quickly possible between two nodes. The important part of the frame level protocols resides in the frame structure and in how to recognize and treat the shortest time possible.
The first feature relates to implement the recognition of the beginning and the end of the frame when the stream of binary information arrives at the receiver. How recognize the last bit of a frame and the first bit of the next frame? Several protocols generations have followed to try and provide the best answer to this problem:
• The first generation of frame-level protocols involved recognition by flag: the beginning and the end of the frame were identified by the presence of a Following bits, to be unique. For this purpose, the insertion techniques were used to break the suites that look like the beginning of a field or end, called flag. The insertion of this additional bit However, a disadvantage, since the total length is not known in advance and that specific mechanisms are required to add these bits to the transmitter and then the subtract from the receiver.
• The second generation tried to find other recognition modes, mainly violations of codes or systems using keys to locate the beginning and end of a frame. The advantage of these techniques is to impart to the frame a length determined and not lose any latency on arrival.
• The tendency of the present generation is to go back to the first solution but flag with a sufficiently long so that the probability to find the same result of bits is almost zero. The advantage of this solution is to allow a simple recognition of the flag without adding bits or to calculate the key value. The Ethernet frame fits this definition with a flag, called a preamble with a length of 64 bits.
The functionality level of the weft have been heavily modified since the early 1990s was done, for example, down into this layer functions of the network layer, to simplify the architecture and increase performance. the level playing field once the role of the network layer and not that of the layer link, for which it was originally designed, acquiring an important status in the delivery data to the receiver. The figure illustrates the potential roles of the frame level relative to the reference model.
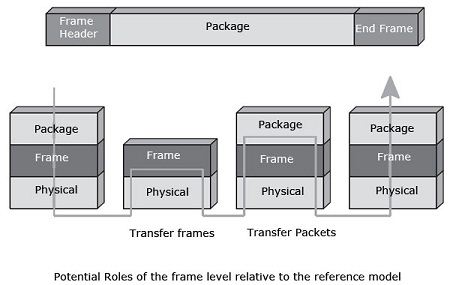
The major protocols used by the frame level are:
• The protocols from the international standardization or taking birth there, such as basic protocol and HDLC and its derivatives LAP-B (Link Access Procedure-Balanced), LAP-D (Link Access Procedure for the D-channel), LAP-F and PPP.
• The protocols designed for the local environment, including Ethernet, Token-Ring and FDDI (Fiber Distributed Data Interface). The Ethernet frame, which is by far the largest.
The ATM standard ITU-T architecture can also be considered as a layer network having inherited a frame structure.
The frame level may have the additional function of managing access to the medium physical, such as in networks having a shared communication medium. This is called MAC function (Medium Access Control).
Frame level Addressing
As indicated above, the frame level is derived from the level of binding of the model reference. The address has not been specifically studied so, since he had to be taken into account by the network level. Typically, the addresses will be very simple: an address for the sender and the receiver. We can complicate this model not having a point-to-point link but a multipoint connection, in which several machines share the same support.
The first address for multipoint networks appeared in the frame level comes from the Ethernet environment and shared LANs. Like all of a customers shared local network connect on the same cable, when a station transmits each station can receive a copy. This is called the distribution function. The addresses have emerged in this context as it required that a station can distinguish frame intended for him a frame to another user. The Ethernet address was thus born of local concerns. We often speak physical address because the address is in the connection card. We had to avoid two cards; even from different manufacturers have the same address. The address took a flat structure, or absolute. Each Ethernet card manufacturer has a constructor number of 3 bytes. At this value, just add a serial number, also on 3 bytes, for a unique address. Since there spread to the shared local network, it is easy to determine where physically located the address of the receiver.
New problems have arisen with the arrival of the new generation Ethernet replacing the broadcast mode by a transfer function of frames, referred to as commutation Ethernet. The reference used for this switching is simply the address 6 bytes of the recipient’s card. An additional field in the Ethernet frame has was added to have a real reference, independent of the Ethernet address. This area with the shim label is particularly used in MPLS networks.
The ATM cell also place at frame: the beginning of the cell is detected by counting the number of bits received because the ATM cell has a constant length. In case of loss synchronization, it is always possible to find the first bit of a grace cell the field detection and error correction that is in the header. ATM using a switched mode, the header contains a reference.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular