• Signature is the proof to the receiver that the document comes from the correct entity. The person who signs it takes the responsibility of the content present in the document.
• A signature on a document, when verified, is a sign of authentication; the document is authentic.
• In the networked world, there is a similar need for digital signatures.
•. Authenticating messages using digital signatures requires the following conditions to be met:
1. The receiver should be able to verify the claimed identity of the sender. For example, an imposter may advise a bank to transfer money from the account of another person. The bank should be able to verify the identity of the user before acting on the advice.
2. The sender should not be able to repudiate the contents of the message it sent at a later date. For example, a person having sent advice to transfer money from his account should not be able at later date to repudiate the content of the message sent by him. The bank should be able to prove that he and only he sent the advice and that the contents of message are unaltered.
3. The receiver should not be able to alter the message or concoct the message himself on behalf of the sender. This requirement is important to protect the interests of the sender.
• Some important features of digital signatures are:
1. When a document is signed digitally, signature is sent as a separate document. The receiver receives both documents i.e. the message and the signature and verifies that the signature belongs to the supposed sender.
2. In order to verify the digital signature, the receiver applies the verification technique to the combination of the message and the signature.
3. In digital signature, there is one to one relationship between a signature and a message. Each message has its own signature. The signature of one message cannot be used for another message.
We’ll be covering the following topics in this tutorial:
Keys in digital signature
• The sender signs the document using his private key by applying it to a signing algorithm.
• The verifier uses the public key of the signer, applied to the verifying algorithm to verify the document.
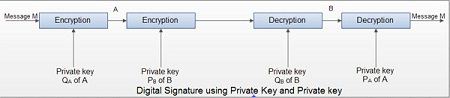
Digital signature using Private Key
• Public and private keys possess the property that allows mutual reversal of their roles, i.e. d, the decryption key can be used for encryption and e, the encryption key can be used for decryption. This property can be used for generating messages with digital signature.
• Suppose A encrypts a message using its private key QA and sends it to B.
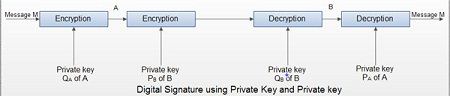
• Since the message has been encrypted using A’s private key it bears A’s signature on it. B already knows A’s public key PA and decrypts the message received from A.
• The received encrypted message is decrypted using A’s public key. So the message is from A.
• B keeps a copy of the encrypted message so that A cannot refuse sending it.
• B cannot alter the encrypted message or on its own concoct the encrypted message without A’s private key.
• The weakness of this mechanism is that any intruder knowing A’s public key can intercept the message.
• Confidentiality is maintained by second encryption using B’s public key.
• A encrypts the message to B using its private key first and then using B’s public key.
• B encrypts the received message using its private key and then using A’s public key.
Digital Signature using Private Key and Message Digest
• This method applies private key digital signature to the digest of the message rather than message itself.
• The basic mechanism used is:
1. This message digest, which is much shorter in length than the message, is encrypted using private key of the sender (A).
2. Message digest and the message are sent to other end (B). B computes message digest of the received message part. The encrypted message digest part is decrypted using A’s public key. The received message digest and the computed message digest are compared to ensure they are same.
3. All the requirements of digital signature are met:
(i) The message digest bears A’s signature. Therefore, A cannot repudiate his signature and the contents of the message digest.
(ii) B cannot alter the content of the message because it cannot generate the message digest bearing A’s signature.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular