The user generates IP packets, it is necessary to transport these IP packets to the ADSL modem. For this, we use an Ethernet frame, a PPP frame, a USB frame, or a superposition of these frames as a PPP frame encapsulated in an Ethernet frame or a PPP frame encapsulated in a USB frame.
Take the example of IP packets encapsulated in an Ethernet frame. This frame is sent either over an Ethernet network connecting the client PC to the modem or in a PPP frame to a USB type interface. In the ADSL modem is uncap the frame to retrieve the IP packet and encapsulate it again, but this time in an ATM frame. This fragmentation into pieces of 48 bytes is achieved through an AAL-5 layer (ATM Adaptation Layer type 5).
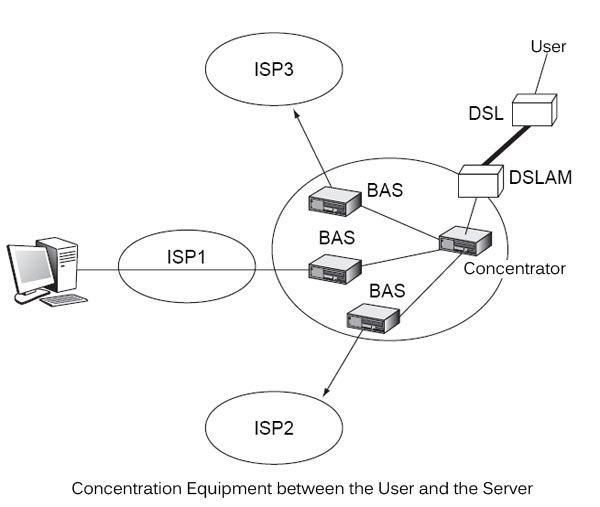
After arrival in the frame ATM DSLAM, several scenarios can Next introduce the architecture of the ISP network to which the client is connected. a first solution is to uncap the ATM cells and recover the IP packet is transmitted to the hub in an Ethernet frame. The hub sends to the ISP also in an Ethernet frame. A second solution is to let form ATM frames. This is the case when the operator of the local loop and ISPs use the same technology. In this case, the ATM cell is sent directly to the hub, which acts as the ATM switch. It sends the ATM frames through virtual circuits to BAS (Broadband Access Server), which are intermediate equipment to access networks of alternative ISP.
These topologies are illustrated in Figure.
Another solution, which is also widely used, is to place the starting IP packet in a PPP frame and retaining said frame along the path, even in the encapsulate other frames. This gave birth to the PPPoE (PPP over Ethernet) in the where the PPP frame is sent to Ethernet. PPP frame may be encapsulated in ATM several frames after being cut into pieces of 48 octets through the AAL-5 protocol.
The advantage of keeping the PPP frame along the way is to encapsulate it in an L2TP tunnel, as we shall see.
L2TP
To realize communication between BAS and servers, a tunneling protocol must be implemented since this path may be considered to be taken by all packets or frames from different DSLAMs and going to the same server. Tunneling is a common technique, which looks like a virtual circuit. The three protocols are used for this PPTP (point-to-point tunneling protocol), L2F (Layer 2 Forwarding) and L2TP (Layer 2 Tunneling Protocol). These protocols allow the user authentication, dynamic address assignment, encryption of data and possibly compression.
The most recent protocol, L2TP, hardly support scaling, or scalability, and fails to properly handle and fast enough a number of flows in excess of the average values. In this case, is added L2TP access concentrator LAC or (L2TP Access Concentrator), which recover all clients from a single DSLAM and going to the same DOWN and multiplex on the same virtual circuit.
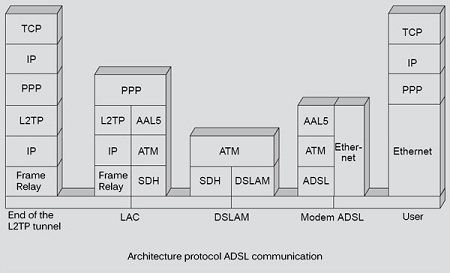
The figure illustrates the protocol architecture of a communication from a PC to a server located in a different ISP network from that of the input operator. The PC works under TCP / IP and is connected to a DSL modem via an Ethernet network.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular