The major objective of network design is to select the network service and to determine the transmission speed for the system. Following are the typical examples of network using WAN and network services:
We’ll be covering the following topics in this tutorial:
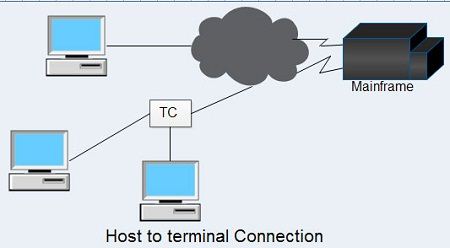
Host to Terminal Connection
The host to terminal connection is a conventional type of connection between a mainframe and dumb terminals. This connection is widely used for routine work. Fixed message length, for example, makes estimation of traffic easy. As terminals are relatively slow, telephone network, low speed leased line, packet switching network, ISDN and so on are mainly used. A terminal controller (TC) may be used to integrate two or more terminals for connection with a high-speed line. The TC shown is used to integrate two or more terminals for connection with a single WAN line.
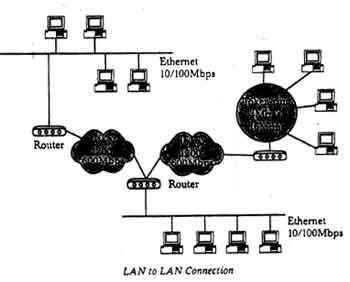
LAN to LAN Connection
The configuration is used to connect LANs that are remote from one another. There is a large difference in transmission speed between LAN and WAN. In addition, using a high speed line can become substantially expensive. Therefore, proper arrangements must often be made to reduce traffic within the WAN. Leased line, ISDN, and frame relay are mainly used for this connection.
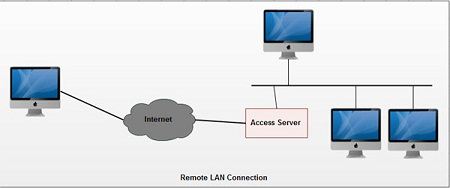
Remote LAN Connection
The configuration is mainly used to connect a remote LAN and PC. Due to the limited number of terminals to be connected and also due to restrictions on allowable expense, the types of WAN that can be used are also limited. In general ISDN is frequently used. Some servers are exclusively designed for the access purpose.
LAN to LAN Connection
Router Concepts
A router has two functions as follows:
- Forwarding Function It is a function that allows selection of the appropriate route based on IP header information and sends packets through this route.
- Filtering Function It is a function that allows dumping of invalid packets for a specific network instead of forwarding.
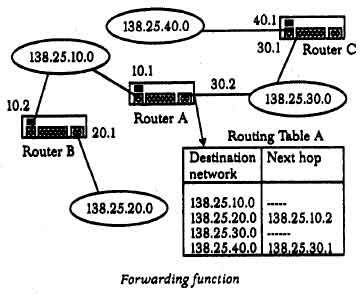
Forwarding Function
The most important processing in forwarding is to determine the route. In general, routing refers to the processing used for determining the next hop (IP address of next router). Here, we consider that the processing for sending packets to the host in the same network is also performed as an integral part of routing. Routing in the same network may be termed as local routing.
The routing is simple if the destination address of the host is in the same subnet. However, if it is not in the same subnet the packet must be sent to the boundary router first. The boundary router references the routing table to determine the next hop. Routing table varies in configuration depending on the routing method used. In this section we will understand the typical hop-by-hop routing table.
The routing table possessed by a router includes combination of destination address and the next hop that corresponds to that address.
The routing table for router a (address 138.25.10.1).This table lists destination addresses for each local network, and not for each destination· host. This table also includes as the next hop (the address of next router) to which the packet must be transferred. If no hops are included, this means that the destination network is directly connected to the router.
When router A receives a packet, it tracks this table to perform routing. For example, if the packets addressed to the host of network 138.25.40.0, then router A sends the packet to router C (138.25.30.1). Router C has a similar routing table so that it can perform routing.
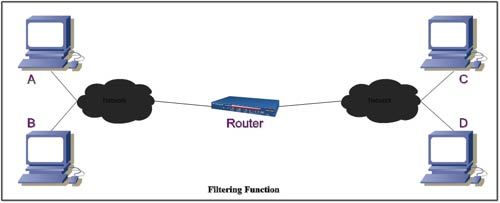
Filtering Function
The second function available with a router is that it can filter packets to determine whether they can pass through it. For example, consider that there are two networks connected via router.
Now, we impose the following conditions:
1. Hosts A and C cannot communicate using UDP packets
2. Host B cannot use FTP for communication with host D
3. Host C cannot communicate with host A
4. Host D can communicate with host B only using TELNET.
In this case the network administrator sets the router as given below:
Exclusion List
(Source host == A, Destination host == C, Protocol == UDP)
(Source host = C, Destination host = A, Protocol = UDP)
(Source host = B, Destination host = D, Port = FTP)
(Source host == D, Destination host = A)
Inclusion List
(Source host = D, Destination host = B, Protocol = TELNET)
Routing Method
Routing plays a major role in the forwarding function. This can be divided into following two methods:
- Static routing: Routing information is manually specified. It provides fixed route information to each router. If there is no change in route, it is made manually.
- Dynamic routing: Routing information is automatically updated by routers when changes are made to the network configuration. It is convenient, as it does not involve human intervention in case of changes to the network configuration. Its disadvantage, however, is that the overhead required to send configuration change information can be a heavy burden.
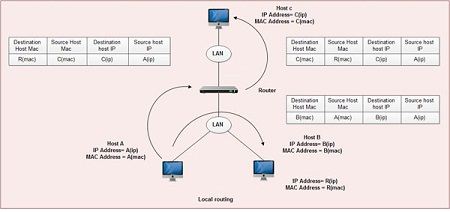
Local Routing
If a packet sent from the source host is addressed to a host in the same subnet, the IP layer of the source host must obtain the MAC address of the destination host.
If a packet is addressed to a host outside the subnet of the originating host, the IP layer must search for a router to relay the packet and obtain the MAC address of that router to send the packet. Therefore, processing required for transferring a packet from the source host to the destination host or to the relaying router is called local routing.
When host A communicates’ with host B over the same LAN, addresses are specified as shown below:
Originating host IP address = A (ip), Originating host MAC address = A (mac)
Originating host IP address = B (ip), Originating host MAC address = B (mac)
On the other hand, when host A needs to communicate with the host C via router R, communication is. achieved in 2 stages, first from host A to router R, and then router R to host C.
Host A Router R
Source host IP address = A (ip), Source host MAC address = A (mac)
Destination host IP address = C (ip), Destination host MAC address = R (mac)
Router A Host C
Source host IP address = A (ip), Source host MAC address = R (mac)
Destination host IP address = C (ip), Destination host MAC address = C (mac)
It is important to note that MAC addresses change while IP addresses remain the same.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular