Routing is the primary element of an ad-hoc network. It takes routing software in each network node to manage the transfer of IP packets. The simplest solution is obviously to have a direct routing, as illustrated in Figure, in which each network station can directly reach another station, without going through an intermediary. The simplest case corresponds to a small cell, with a diameter less than 100 m, as in an 802.11 network in ad-hoc mode.
The classic case of routing in an ad-hoc network is to pass through intermediate nodes. They must have a routing table adapted to direct the packet to the recipient. The whole strategy of an ad hoc network is to optimize the routing tables for updates more or less regular. If the updates are too regular, it can overload the network. However, this solution has the advantage of maintaining updated tables and therefore allow rapid packet routing. An update only when the arrival of a new wave restricted load circulating in the network, but unloads the many streams supervision network.
It should happen in this case to set up routing tables may make the delivery within an acceptable time.

Figure illustrates the case of an ad-hoc network in which, to get from one node to another, it may be necessary to traverse the intermediate nodes. Many pitfalls can be on the road to building the routing table. For example, signal for transmission, it is possible that the connection is not symmetrical, a sense of communication are acceptable and not the other. The routing table should reflect this. The radio signals are susceptible to interference; asymmetric links can also be complicated by possible fainting links.
For all these reasons, the network routes to be constantly modified, hence the eternal question discussed at the IETF: should maintain the routing tables in the nodes of a mobile ad-hoc network? In other words, is it worthwhile to keep updated routing tables ever changing, or is it not more sensible to determine the routing table denier now?
As explained above, the reactive protocols work by flooding to determine the best route when a packet stream is ready to be issued. So there is no exchange of outside supervision control packets to determine the path of the flood. The supervisory packet which is broadcast to all neighboring nodes is played again by the neighboring nodes to reach the receiver. Depending on the chosen technique, one can avail of the road determined by the first supervision package that arrives at the receiver or provide several routes in case of problems on the main road.
Proactive protocols behave totally differently. Supervision packets are transmitted continuously in order to keep updated the routing table by adding new lines and removing some. The routing tables are dynamic and change according supervision packets arriving at the various nodes. A difficulty in this case is to calculate a routing table that is compatible with the routing tables of the different nodes so that there is no loop.
Another possibility is to find a compromise between the two systems. That is to regularly calculate routing tables as the network is lightly loaded. Thus, the performances of user streams in transit are not too changed. When traffic increases, the updates are slowed. This method simplifies the implementation of a reactive routing table when a request reaches the network.
The proposed protocols for the normalization of the group are summarized in MANET Table. Different metrics can be used to calculate the best Road:
• The distance vectors give a weight to each link and add the weights to determine the best route, which corresponds to the least significant.
• The source routing to determine the best route as one that allows the supervision package to arrive first to the recipient.
• The states of links indicate the links that are interesting to take and those who are less so.
Metric | Reactive | Proactive |
Vector distance | AODV (Ad-hoc On demand Distance Vector) | DSDV (Destination Sequence Distance Vector) |
Source routing | DSR (Dynamic Source Routing) | |
Link Status | OLSR (Optimized LinkState Routing Protocol) |
In conclusion, if MANET group studies are almost finished regarding routing, almost everything remains to be done to the quality of service, safety and power consumption.
The following briefly describes the two main routing protocols in ad hoc networks MANET standardized by the group.
We’ll be covering the following topics in this tutorial:
OLSR (Optimized LinkState Routing)
OLSR (Optimized Link State Routing) is certainly the most used ad-hoc routing protocols. It is proactive type.
To avoid carrying too much supervision packets, OLSR relies on the concept of multi-point relays, or MPR (Multi-point Relay). The CPMs are important nodes that have the distinction of being the best crossing points to reach all the nodes in a flooding process without spreading in all directions. The link state being sent by the MPR, it reduces all supervisory posts.
Knowledge of its neighbors is obtained by Hello messages that are sent in broadcast. This helps to identify the neighbors and to send the information status necessary link to the routing algorithm. The Hello messages also indicate the MPR to its neighbors. These Hello messages are intended only neighboring nodes and can not be routed to a destination with two jumps. The structure of the Hello packet is illustrated in Figure.
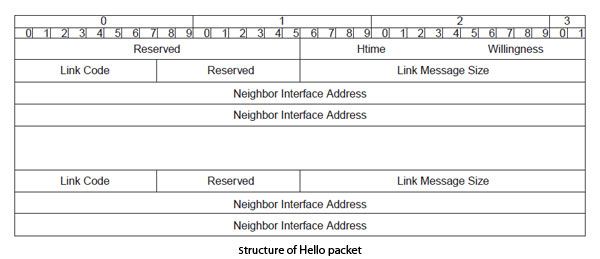
The Reserved field contains only 0, the HTime field indicates the time interval between Hello, Willingness the application field to a node to become a MPR, the Link Code field to pass the link state information between transmitter and receivers indicated in the list of “Neighbor Interface Address”.
TC packets (Topology Control) are issued only by the MPR, always with a broadcast address. The transmitted information indicates a list of all the neighbors that have chosen this node as MPR and allows, through the knowledge of all MPR and link state, to deduce the routing table. These messages are broadcast across the network with a value of 255 in the TTL field. The structure of the TC packet is shown in Figure.
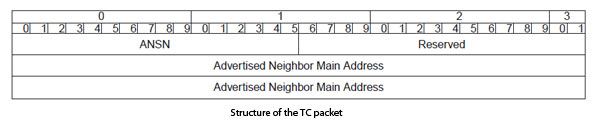
The Reserved field is always filled with 0. The field ANSN (Advertised Neighbor Sequence Number) transports an entire incremented each topology change. This trick allows not consider information that would be too old. Fields Advertised Neighbor Main Address carries the IP addresses of nodes at a jump.
The packages MID (Multiple Interface Declaration) are used when the nodes have multiple interfaces and must report all available interfaces.
The MPR selection algorithm is as follows. With Hello messages, the nodes can determine whether they are connected in full duplex to their neighbors. The determination of the MPR considers only symmetric links. Compared to a given node, a first set is determined, its neighbor’s one hop, the set A. To determine the MPR, Hello messages are rerouted, allowing determining the two-hop nodes which form another well-defined set, the set B. Each node determines the symmetrical links with its neighbors. For all B nodes that have one and only one with a symmetrical knot A, we define it as MPR node A, and no longer take account of B nodes connected by this MPR. It repeats the process until there are no more unbound in Node B. The MPR nodes are then all determined.
AODV (Ad hoc On-demand Distance Vector)
AODV (Ad hoc On-demand Distance Vector) was the first standardized protocol by MANET group just before OLSR. It is reactive type. This protocol can handle both uni-cast and multicast routing.
When a packet stream is output from a node, the first action is to determine the road by a flooding technique. For this, the connection request packet stores the nodes crossed during the broadcast. When an intermediate node receives a connection request, it checks it has not already received such a request. If the answer is positive, a message is returned to the sender to indicate the abandonment of that road.
The first message that arrives to the recipient determines the route. The complexity of the route determination process should be as simple as possible by avoiding unnecessary broadcasts. For this, each application request opening of a road is numbered, to avoid duplication’s and has a TTL which limits the number of transmissions in the network.
The advantage of AODV is not to create traffic when there is no message to transmit. The determination of the road is quite simple and involves little calculation in each node. It is obvious that the two major disadvantages are time implementation of the road and the important traffic generated to develop the roads.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular