A network is a set of computers connected through a transmission medium, to transmit and receive information from other computers in the network. You can also define a network as a set of devices (often called nodes) connected by links from a physical medium. A node can be a computer, a printer, or any other device capable of sending and receiving data generated by other nodes of the network. The links connected to the devices, often referred to as communication channels.
The main objective of any computer network is to exchange information between two entities. The figure shows a particular example of communication between a workstation and a server through a public telephone network. Another possible example is the exchange of voice signals between two telephones through the same previous network.
The source: This device generates the data to be transmitted: for example, telephones or personal computers.
Transmitter: Normally, the data generated by the source is not transmitted directly as it generated. On the contrary, the transmitter transforms and encodes the information producing electromagnetic signals susceptible to be transmitted through some transmission system.
The transmission system: That can be from a simple transmission line to a complex network that connects the source with the destination.
The receiver: That accepts the signal coming from the transmission system and converts it in such a way that the target device can handle it. For example, a MODEM accepts the analog signal from the network or transmission line and convert it into a bit string — the destination, which takes the data from the receiver.
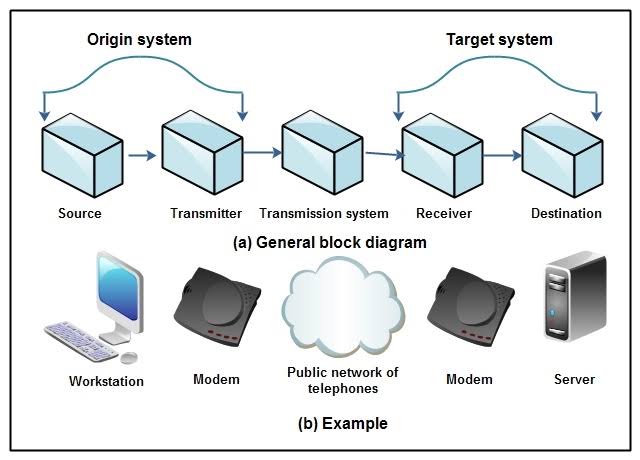
Although the presenting model may seem seemingly simple, it implies great complexity. The magnitude of the complexity of the critical tasks to be performed in the communication system are: use of the transmission system (addressing), implementation of the interface (routing), generation of the signal (recovery), synchronization (message format) , exchange management (security), detection and correction of errors (network management), flow control.
Now, we talked about what a communication system should have in general; then we will see the essential criteria of a computer network.
To be considered valid and efficient, a network must satisfy a certain number of criteria. The most important are Benefits, reliability, and security.
We’ll be covering the following topics in this tutorial:
Benefits
Benefits can measure in many ways, including transmit time and response time. Transit time is the amount of time necessary for a message to travel from one device to another. The response time is the time between a request and a response.
The performance of a network depends on several factors, including the number of users, the type of transmission medium, the capabilities of the connected hardware devices, and the efficiency of the software.
The number of users: The existence of a large number of concurrent users can delay the response time in a non-designed network to coordinate a large volume of traffic. The design of a network based on an estimate of the average number of users who will be in communication at the same time. The way a network responds to the load is a measure of its performance.
Type of transmission medium: The medium defines the speed at which data can send through a connection (the data rate). The current networks are increasingly getting more and faster means of transmission.
Hardware: The type of hardware included in the network affects both the speed and the transmission capacity of the same. A high-speed computer with a large storage capacity results in better performance.
Software: The software used to process the data in the sender, the receiver, and the intermediate nodes also affect the network’s features. Bringing a message from one node to another through a network means a specific processing load to transform the primary data to transmissible signals, to route these signals to the appropriate destination, to ensure error-free delivery and to reconvert the signals into a format that the user can use. Well, designed software can speed up the process and make the transmission more effective and more efficient.
Reliability
In addition to taking into account the accuracy of the delivery, the reliability of the network measured by the frequency of failure, the time it costs to recover from the failure and the robustness of the network within a catastrophe.
Fault frequency: All networks fail occasionally. However, a failing network is often very useless to users.
Recovery time of a network after a failure. How much does it cost to restore the service? A network that recovers quickly is more useful than one that does not.
Catastrophe: Networks must protect from catastrophic events such as fires, earthquakes, and robberies. Proper protection against unforeseen damage, to achieve a reliable network system, that is, to have backup copies of the network software.
Security
The security aspects of the network include data against unauthorized access and viruses.
Unauthorized access: To be useful, sensitive data must protect against unauthorized access. Protection can be carried out at a certain number of levels. At the lowest level the user identification codes and passwords. At a higher level are encryption techniques. With these mechanisms, the data systematically altered so that if an unauthorized user intercepts them, they are intelligible.
Virus: Because the network is accessible from many points, it can be susceptible to computer virus attacks.
Applications
In the short space of time they have been operating, data transmission networks have become an indispensable part of business, industry, and entertainment. Some of the applications of the networks in the different fields are the following:
Marketing and sales: Computer networks are used extensively in marketing and sales organizations. Marketing professionals use it to collect, exchange, and analyze data related to customer needs and product development cycles.
Financial services: Financial services are currently totally dependent on computer networks. Applications include credit history search, foreign currency exchange.
Manufacturing: Computer networks currently used in many areas of manufacturing, including the manufacturing process itself. Two applications that use networks to provide essential services are computer-aided design (CAD) and computer-aided manufacturing (CAM), which allow multiple users to work simultaneously on a project.
Electronic messaging: One of the most widespread application is email.
Directory services: The directory services allow to store lists of files in a centralized location to accelerate the technical operations for a new product is an information service.
Information services: The information services of the network include newsletters and data banks. A web server that offers technical specifications for a new product is an information service.
Electronic data exchange (EDI): The EDI (Electronic Data Interchange) allows the transmission of commercial information (including documents such as orders and invoices) without using paper.
Teleconference: The teleconference allows to carry out conferences without the participants being in the same place. Applications include simple text conferences (where participants communicate through keyboards and computer monitors), voice conferences (where participants in a certain number of locations communicate simultaneously over the phone) and video conferencing (where participants can see while talking to each other).
We have presented 4 basic criteria that are considered in a network system (performance, reliability, security and applications), now it is important to illustrate the simplified model of computer networks which suggests two major categories in which are traditionally classified networks: wide area networks (WAN, Wide Area Networks) and local area networks (LAN, Local Area Networks).
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular