IEEE 802.5 Token Ring: Token ring is the IEEE 802.5 standard for a token-passing ring in Communication networks. A ring consists of a collection of ring interfaces connected by point-to-point lines i.e. ring interface of one station is connected to the ring interfaces of its left station as well as right station. Internally, signals travel around the Communication network from one station to the next in a ring.
These point-to-point links can be created with twisted pair, coaxial cable or fiber optics. Each bit arriving at an interface is copied into a 1-bit buffer. In this buffer the bit is checked and may be modified and is then copied out to the ring again. This copying of bit in the buffer introduces a 1-bit delay at each interface.
Token Ring is a LAN protocol defined in the IEEE 802.5 where all stations are connected in a ring and each station can directly hear transmissions only from its immediate neighbor. Permission to transmit is granted by a message (token) that circulates around the ring. A token is a special bit pattern (3 bytes long). There is only one token in the network.
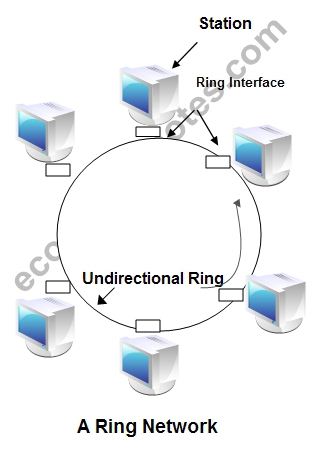
Token-passing networks move a small frame, called a token, around the network. Possession of the token grants the right to transmit. If a node receiving the token in order to transmit data, it seizes the token, alters 1 bit of the token (which turns the token into a start-of-frame sequence), appends the information that it wants to transmit, and sends this information to the next station on the ring. Since only one station can possess the token and transmit data at any given time, there are no collisions.
There are two operating modes of ring interfaces. There are listen and transmit. In listen mode, the input bits are simply copied to output with a delay of 1- bit time. In transmit mode the connection between input and output is broken by the interface so that is can insert its own data. The station comes in transmit mode when it captures the token.
The frames are acknowledged by the destination in a very simple manner. The sender sends frames to receiver with ACK bit 0. The receiver on receiving frames, copies data into its buffer, verifies the checksum and set the ACK bit to 1. The verified frames come back to sender, where they are removed from the ring.
The information frame circulates the ring until it reaches the intended destination station, which copies the information for further processing. The information frame continues to circle the ring and is finally removed when it reaches the sending station. The sending station can check the returning frame to see whether the frame was seen and subsequently copied by the destination.
A station can hold a token for a specific duration of time. During this time, it has to complete its transmission and regenerates the token in ring. Whenever a station finishes its transmissions, the other station grabs the token and starts its own transmission.
Handling cable breakage in ring networks
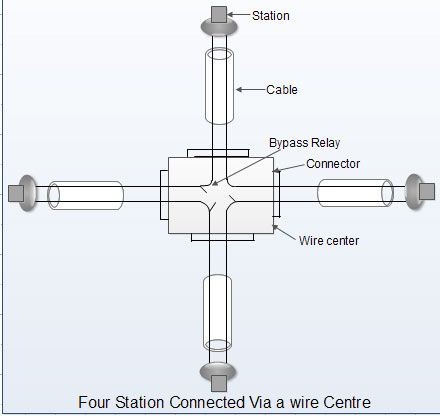
• If the cable breaks, the entire ring network goes down. This can completely stop the propagation of token in the ring.
• This problem can be solved by using wire centre as shown in fig.
• This wire centre bypasses the terminal that has gone down in following manner:
(a) Each station is connected to wire center by a cable containing two twisted pairs, one for data to station and one for data from the station.
(b) Inside the wire center are bypass relays that are energized by the current from the stations.
(c) If the ring breaks or a station goes down loss of drive current will release the relay and bypass the station.
We’ll be covering the following topics in this tutorial:
Physical Layer of Token Ring
The cable recommended for a token ring by IEEE 802.5 contains two pairs of twisted-cables covered by a shield. Signal speed of this media is 1 Mbps or 4 Mbps. But IBM released a Token ring version that can operate at a speed of 16Mbps. The adapter for this also supports 4 Mbps. Differential ‘Manchester’ encoding scheme is used for encoding the digital data. Any single point failure on the cable may cause the ring to disappear instantly. Special devices called wire centers are used to bypass the bad segment of the cable or the problematic stations.
MAC Sublayer Protocol
The MAC sub layer is on the top of the physical layer. The protocol is defined as follows.
When there is no traffic on the ring, a 3-byte token circulates continuously until some station grabs it. The station, which acquires the token, changes a specific 0 bit into a 1 bit, thus converts a token frame into a start of frame sequence. The station then transmits the normal data frame sequence. The length of the frame may be long or short. When it is long, the first bit of the transmitted frame completes the round trip through the ring and comes back to the sender before the completion of the current frame. The sender has to remove the bits that have completed their round trip. The maximum time a station is permitted to hold the token is known as token holding time. A station can send any number of frames within the time. As soon as the time is over, it should regenerate the token and put it on the ring.
IEEE 802.5 Token Ring Frame Format
The IEEE 802.5 Token ring frame format is shown in Figure.
Start of frame and end of frame: Used to mark the beginning and end of the frame. The patterns used do not contain the differential Manchester coded patterns. Hence, these patterns can be distinguished from the useful data field.
Access control The access control field is used to represent the three-byte token along with the start of frame and end of frame. When the station starts transmitting, this field is used to perform monitoring, reservation, priority.
Frame control This field is used to discriminate the data field from the other fields.
Source address and destination address These fields are same as IEEE802.3 and IEEE 802.4 protocol.
Check sum This field is also same as the check sum field of earlier protocols.
Token Ring Maintenance
The following are a few ring management activities.
Monitor stations Each ring has a monitor station that performs monitoring the ring. It also takes appropriate action when the ring is broken. It also clears the ring when there are garbled frames on the ring. If the monitor station fails, some other station is chosen by means of a special contention protocol.
Ring Initialization When the network is powered up, initially there is no monitor. The first station on the network transmits a claim-token frame. If there is nothing else, a claim-token frame is setup the first station becomes the token owner as well as the monitor.
Lost tokens The monitor station has an internal timer that is set for the longest possible time interval without a token. If the token is not produced within the period, the monitor station clears the ring and issues a new token.
Orphan frames Stations crashed after transmitting a short frame form orphan frames. The transmitted frame simply circulates around the ring. The monitor station sets the monitor bit in the access control byte whenever a frame passes through it. If a frame already contains this bit set that means the frame is passing through the monitor for the second time. The monitor immediately removes it from the ring.
Token Ring Protocol
Token ring LAN is an ideal network in a typical office environment — all the stations connected in the form of a ring. A station has to acquire a token before the start of transmission. The frame transmitted by a station makes a full circulation and comes back to the originating station. All intermediate stations receive and retransmit the frame.
MAC protocol All stations connected in the form of a ring. Only one station seizes the token, and all the other stations must wait for the token. Every transmitted frame revolves around the ring and finally absorbed by the transmitting station. If the frame is shorter, the first bit of the frame completes its round trip transit and comes back to the sender after the release of the last bit. In this case, the transmitting station inserts a new token into the ring after the completion of the current frame transmission. However, for frames with the longer length, the station completes the transmission after the leading edge is received. In case, the station releases the token immediately after the release of the last bit, then the method of release is known as an early release. When a station releases a token, the immediate next station waiting with the data seizes the token and starts the transmission. Token ring scheme is inefficient if there are very few stations ready with data. When all stations are busy, fairly proper utilization of the ring is possible. The main drawback of the token ring is ring maintenance. Loss of token and duplicate tokens are significant issues in token maintenance. The following section describes more details about the IBM Token Ring Network features.
The IBM Token Ring Network
The IBM Token Ring Network is a Local Area Network, based on a token-passing access method. This Token passing method consists of a particular frame, called a token, which continuously circles the network medium, known as the ring. A station that needs to communicate with another station must obtain the token, change it from free to busy, append any relevant data, and transmit the information. The receiving station recognizes that the frame directed toward it by addressing information embedded in the data, and it copies the data into its internal buffers and then releases the frame back onto the ring. The station that initially sent the data, on receipts of the frame that is transmitted, examine any frame status information that was set by the second station, remove the data from the ring, and release a free token. The next station on the ring then have the opportunity to transmit data if necessary, or else it passes the free token onto the next station. This procedure continues indefinitely.
The token ring operation does not suffer from the well-known collision problem because only one station has access to the token at one point in time. It does not imply that only one station may have data on the ring at one time. The IBM Token Ring Network allows multiple frames to be present on the ring at the same time, but access to the free token is still mutually exclusive. In addition to that, IBM’s network also ensures that data frames do not circle the ring indefinitely and that all stations on the network are uniquely addressable. The Token ring adapter uses a particular chipset to ensure the integrity and smooth operation of the token-ring network. Some of its functions described below.
Ring monitor: The adapter acts as an active monitor to perform duties such as token monitoring and ring clock. These duties include removing frames that circulate the ring indefinitely. It also lowers the priority of a free token if the station that released the token has failed to lower its priority. In case, the active monitor fails, it acts as a standby monitor.
Ring Error Monitor (REM): Collects errors, which occur, on the token ring. These include hard errors, which may indicate ring and station failures and soft errors, which do not affect the integrity of the network.
Ring Parameter Server (RPS): When stations inserted into the ring, the token ring adapter chipset provides the initialization values.
Configuration Report Server (CRS): To record the current ring in case of failure of one or more stations, the chipset sends requests to collect status information from various stations. This feature can use in conjunction with a higher-level LAN management function.
The token ring is a compatible superset of the standard that is put forth by the Institute of Electrical and Electronics Engineers (IEEE) Standards Board and the American National Standards Institute (ANSI) standard for a ring, utilizing token passing as the access method. IEEE standard 802.5 formed in the year 1989. Data rates for the IBM Token Ring are 4 Mbps and 16 Mbps. Logic to improve throughput further, known as the early token release, is also covered by the latest version of the standard.
IBM Token ring Frame Formats
This section presents the frame structures of the IBM Token Ring network. The IBM token ring has two basic formats, or frames, for transmitted information. The first format, known as the Token Format, consists of three bytes of data and represents the free token. Included within this frame is one byte each for Starting Delimiter (SD) and Ending Delimiter (ED), and one byte for Access Control (AC), used to differentiate between a free token and a data frame. The second format, known as the Frame Format, is used for the transmission of network management and user information. This frame, like the free token, consists of start and end delimiters and Access Control to identify a non-token frame, but it also includes the following additional fields for network management and user information transmission.
Frame Control (FC): Identifies the type of underlying information.
Destination Address (DA): Identifies the receiving station, the frame.
Source Address (SA): Identifies the sender.
Routing Information (RI): Optionally includes source route paths.
Information (INFO): Includes the actual data that transmitted over the token ring network.
Frame Check Sequence (FCS): Includes a Cyclic Redundancy Check (CRC) for detecting transmission errors.
Frame Status (FS): Designates the actions performed on the frame by the remote stations to which it addressed.
Medium Access Control (MAC): MAC performs all the network management actions discussed above. It is also a sublayer to the overall Data Link Control (DLC), which is used for lower layer communication activities in various data communication and network architecture models such as the Open Systems Interconnect (OSI) reference model from the International Standards Organization (ISO), Systems Network Architecture (SNA) from IBM, and Transmission Control Protocol/Internet Protocol (TCP/IP).
Logical Link Control (LLC): LLC is a sublayer of Data Link Control that defines frame formats and protocols for the transmission of connectionless or connection-oriented services. The information generated by the architectures referenced above transmitted within the LLC Protocol Data Unit (PDD) frames. LLC described in IEEE Standard 802.2/1S0 8802.2 The LLC frame format is shown in Figure. LLC frames consist of a Destination Service Access Point (DSAP), a Source Service Access Point (SSAP), one or two bytes of Control Information, and zero or more bytes of Data Information. The Service Access Points (SAPs) used as logical ports, or addresses, from the higher-level communication and network models, such as OSI SNA, and TCP/IP into the LLC sublayer. Communication between two entities on an IBM token ring network will be between addressable MAC/LLC entities.
Addressing
Medium access control address: The IEEE802.5 standard provides two address formats for token ring networks, 16 bit (2byte) and 48 bit (6-byte). All nodes on a network must use the same addressing scheme. Nearly all networks use the 6-byte format shown in Figure.
Three types of addresses used with the IBM token ring network. They are Ring Station Address, Group Address, and Functional Address.
Ring station address: It is used to identify stations on the token ring uniquely. A 0 in bit 0 of byte 0 represents a Ring Station Address. A ‘I’ in this bit position would indicate that the address is a group address. When the ring station address is a source address, this group address indicator bit is no longer relevant for group address identification purposes, since frames can only send from individual ring stations. Instead, a value of ‘I’ in this field indicates that there is source routing information present in the frame.
The bit 1 of byte 0 can be used to select one of the following address administration methods. They are local administration and global administration. In local administration, the network administrator or local management entity manages the addresses. In the globally administered case, the addressing scheme uses the default values that have been assigned by the IEEE and guaranteed as unique. The choice of locally or globally administered addresses is a decision of the network manager; only one of the two schemes should use for an IBM Token Ring Network. In general, globally administered addresses have the benefit of ensuring that all the addresses for ring stations on the network are unique, while locally administered addresses are useful when various network management facilities are in use. An example of this latter case would be to embed an office number in a station address so that the particular device could physically locate through its MAC address alone.
Group addresses: A group address is specified only within the Destination Address field. It is used to identify multiple stations on the token ring. Default group addresses are known as broadcast addresses. All stations on a particular token ring receive when broadcast addresses are specified. The user may choose to define additional group addresses.
Functional addresses: Functional address is a particular type of Group Address, functional addresses are identified by bytes 0 and 1 of the O A set to a predefined pattern. Bit 0 of byte 2 is set to ‘0’, and one or more of the remaining 31 bits in bytes 2 through 5 is set, as necessary. Each of these 31 bits represents network management functions such as RPS and REM, in addition to representing optional features such as token ring bridges.
Logical link control addresses: Logical Link Control (LLC) addresses represented by Service Access Points (SAPs) and are one byte in length.
Each LLC POU consists of two SAPs, one destination and one source (OSAP and SSAP). The bits are defined as follows. Bits 0 to 5 are the actual address bits. Bit 6 identifies whether the SAP address is user-defined if set to ‘0’, or defined by the IEEE if set to ‘I.’ Bit 7 identifies whether the SAP is an individual SAP if set to ‘0’, or a group SAP if set to ‘1’.
Source Routing and Multi-Ring Operation
Rather than have all stations on an IBM Token Ring Network located on a single physical ring, the IBM Token Ring architecture allows for interconnection of multiple rings via token ring bridges. A token ring bridge is a specially configured ring station that interconnects two physical token ring networks. A ring station that has a frame to transmit decide whether the frame is to be transmitted on the local (source) ring or is to additionally transmitted to all rings. The decision to execute a multi-ring transmission depends on the higher-level protocols that exist on the ring station. To have a multi-ring transmission, the originating ring station inserts source routing information into the frame. The presence of source routing information is indicated by bit 0 of byte 0 of the MAC source address is set to 1. This bit position is usually the group address indicator, but group addresses are irrelevant in a source address field since all transmissions are from one station only. Three types of source routes used in an IBM token ring network. They are non-broadcast, all-routes-broadcast, and single route broadcast.
Non-broadcast: Used when a ring station on a remote token ring network knows a route. The originating station transmits the frame with the non-broadcast source route attached. The token ring bridge, depending on how it configured, optionally transmit the frame on its second ring. Configuration issues that determine whether to transmit to the second ring include internal bridge congestion; matching ring and bridge numbers; and most solid frame passable by the bridge.
AII-routes-broadcast: Used when the path to the destination ring station is not known. A bridge is receiving an all-routes-broadcast frame append segment field information, depending on whether or not that specific segment already occurs in the route. Therefore, multiple copies of the original frame, each with different source routing information, may arrive at the destination ring and may also occur more than once on the same ring. The originating station must be prepared to receive multiple responses (usually non-broadcast) and then select the optimum route, depending on such parameters as frame sizes allowable by bridges, the total number of bridges that must cross (that is, number of hops), and response time.
Single-route-broadcast: Used when the path to the destination ring is not known. Bridges are needed to be configured for the single-route-broadcast feature, to use this mode. Single route broadcast bridges communicate with one another and form a spanning tree protocol to represent and continuously update the topology of the network. The result is that the transmitted frame only occur once per ring and the destination ring only receive one copy of the frame. The destination may then respond to the originating station with a non-broadcast frame, containing the routing information of the frame that it just received, or with all-routes-broadcast frame.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular