The Internet Control Message Protocol (ICMP) is an error reporting protocol that is an integral part of the IP protocol. ICMP communicate control data, information data, and error recovery data across the network. Problems that are less severe than transmission errors result in error conditions that can be reported. For example, suppose some of the physical paths in Internet fail causing the Internet to be partitioned into two sets of networks with no path between the sets. A datagram sent from a host in one set to a host in other cannot be delivered.
The TCP/IP suite includes a protocol called ICMP that IP uses to send error messages when condition such as the one described above arises. The protocol is required for a standard implementation of IP. We will see that the two protocols are co-dependent. IP uses ICMP when it sends an error message, and ICMP uses IP to transport messages.
Following is a brief description of some of the error messages defined by ICMP protocol:
- Source Quench A router or host whose receive communication buffers are nearly full normally triggers this message. A source quench message is sent to the sending host, the receiver is simply requesting the sending host to reduce the rate at which it is transmitting until advised otherwise.
- Time Exceeded A time-exceeded message is sent in two cases. Whenever a router reduces the TIL field in a data gram to zero. The router discards the datagram and sends a time exceeded message. In addition, a time exceeded message is sent by a host if the reassembly timer expires before all fragments from a given datagram arrive,
- Route Redirect A router sends this message to a host that is requesting its routing services. When a host creates a datagram destined for a network, the host sends the datagram to a router, which forwards the datagram to its destination. If a router determines that a host has incorrectly sent a datagram that should be sent to a different router, the router uses route redirect message to cause the host to change its route. In this manner, a route redirect message improves the efficiency of the routing process by informing the req4esting host of a shorter path to the desired destination.
- Host Unreachable Whenever a gateway or a router determines that a datagram cannot be delivered to its final destination (due to link failure or bandwidth congestion), an ICMP host unreachable message is sent to the originating node on the network. Normally, the message includes the reason the host cannot be reached.
- Fragmentation and Reassembly The largest datagram the IP protocol can handle is 64 Kbytes. The maximum datagram size is dictated by the width of the total length field in the IP header. Realistically, most underlying data link technologies cannot accommodate this data size. For example, the maximum size of the data frame supported by Ethernet is 1,514 bytes. Unless something is done about situations like this, IP has to discard data that is delivered to it from upper layer protocols with sizes exceeding the maximum tolerable size by the data link layer. To circumvent this difficulty, IP is built to provide data fragmentation and reassembly.
Whenever an upper-layer protocol delivers data segments whose sizes exceed the limit allowed by the underlying network, IP breaks the data into smaller pieces that are manageable within the allowed limit. The small data grams are then sent to the target host, which reassembles them for subsequent delivery to an upper-layer protocol.
Although all data fragments are normally delivered using the same route, in some situations a few of them might traverse alternative routes. Fragments following different routes, however, stand the chance of reaching their-destination out of the order in which they were sent. To allow for recovery from such behaviour, IP employs the fragmentation-offset field in its header. The fragmentation-offset field includes sequencing information that the remote IP host uses to recover the sequence in which the data grams were sent. IP also uses the information in the fragmentation offset field to detect missing fragments~ Data is not passed to the protocol described in the protocol field unless all related fragments are duly received and reordered. This process of fragment recovery and re-sequencing is called data reassembly.
Fragments belonging to two or more independent large data can be differentiated by IP using identification field. Fragments belonging to the same datagram are uniquely assigned in the identification field. The receiving 110stuses this number to recover the IP fragments to their respective data grams.
A host that creates a datagram can set a bit in the flag field to specify the fragmentation. Among other bits, the flag field includes a more fragments bit, which is set to I in all fragments belonging to a datagram except for the final fragment. This ensures about the receiving of all fragments of a datagram.
- Echo request/Echo reply – These two ICMP messages are exchanged between ICMP software on any two hosts in a bid to check connectivity between them. The ping command is an example of a diagnostic command commonly used by network users to check for the reach ability of a certain host. Whenever ping is invoked at the command line, ICMP echo request message is sent to the target host. If the target host is operational and connected to the network, it responds with an echo reply message as proof of reach ability. In other words, the reply carries the same data as the request.
- Address Mask Request/Reply A host broadcasts an address mask request when it boots, and routers that receive the request send an address mask reply that contains the correct 2-bit subnet mask being used on the network.
We’ll be covering the following topics in this tutorial:
ICMP Message Transport
ICMP uses IP to transport each error message. When a router has an ICMP message to send, it creates datagram and encapsulates the ICMP message in the datagram. It means that the ICMP message placed in the data area of the IP data gram. The· datagram is forwarded as usual with the complete data gram being encapsulated in a frame for transmission.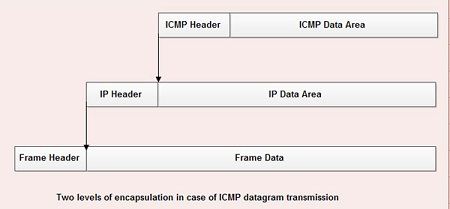
Passing Data to Other Protocols
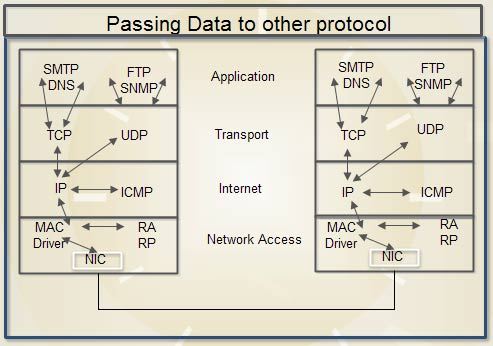
As we know from the previous section that all TCP/IP protocols send their data in IP datagrams. Illustrates how data is exchanged across protocol boundaries. A protocol field that is included in IP header assists IP in passing data to other protocols. By TCP/IP standards, each protocol that uses IP routing services is assigned a protocol identification number. Setting the protocol field to 6, for example, designates the data as belonging to the TCP protocol, whereas it designates the ICMP protocol. A protocol number of 0 designates the IP protocol, in which case encapsulated data is processed by IP itself.
The Transport or Host-to-Host layer
The host-to-host layer, also known as the Transport layer, corresponds to the transport layer of the OSI model. Protocols defined at this layer accept data from application protocols running at the application layer. Protocols encapsulate it in the protocol header, and deliver the data segment thus formed to the lower IP layer for subsequent routing. Unlike the IP protocol, however, the transport layer is aware of the identity of the final user representative process. As such, the transport layer, in the TCP/IP suite, embodies what data communications are all about the delivery of information from an application on one computer to an application on another computer.
At the transport layer, TCP/IP defines two transport protocols namely User Datagram Protocol (UDP) and Transmission Control Protocol (TCP). Applications can use one protocol or the other depending on the type of service they desire. To associate data with applications, TCP and UDP include Source and destination port number fields in their headers. These fields are used in much the same way as IP uses the protocol field for, the internal routing of data to applications utilizing their services.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular