Data link layer is the second layer in OSI reference model and lies above the physical layer. The physical layer provides only a raw bitstream service between computers. The data link layer provides data reliability and provides tools to establish, maintain, and release data link connections among the network nodes.
The data link Connections between nodes can consist of one or more physical lines. These include copper-wire cable, optical fiber cable, microwave link, and satellite channels. The devices located at the network nodes could be terminals, computers, switching, or other communicating equipment. The information exchanged between the nodes could be of any form, including link-control functions or user data or remote function calls.
The data link layer performs the following functions.
• Data link layer receives the data from the network layer & divide it into manageable units called frames.
• It then provides the addressing information by adding header to each frame. Physical addresses of source & destination machines are added to each frame.
• It provides flow control mechanism to ensure that sender is not sending the data at the speed that the receiver cannot process.
• It also provide error control mechanism to detect & retransmit damaged, duplicate, or lost frame, thus adding reliability to physical layer.
• Another function of data link layer is access control. When two or more devices are attached to the same link, data link layer protocols determine which device has control over the link at any given time.
• Initialization: This function establishes an active connection over an already existing transmission path. It is called link initialization. The data link layer does not worry about how the path is set up, and bits moved as the physical layer takes care of those things. To initialize the link, the peer data link layers, exchange service request, and indication primitives.
• Information segmenting (framing): The process of breaking up a long bit stream into several small, fixed length bit slices is known as message segmentation or framing. When data transmitted in the form of a long bit stream, it is always affected by an error in a noisy environment. Hence, it required to retransmit the entire message. Shorter messages have lower possibilities for error and take small transit time. It is an essential reason for framing.
Apart from framing, the data link layer also attaches control information to identify the start and stop of the frame and to check the possibility of error.
• Error control: Since errors inevitably occur during the transmission; the data link layer must have the ability to detect and correct errors to maintain a high degree of information integrity.
• Data synchronization: The synchronization between transmitter and receiver is essential to ensure that the information received is correct. The data link layer must align the character-decoding mechanism of the receiver to the character-encoding mechanism of the transmitter.
• Flow control: Consider a transmission process in which the sender is faster than the receiver. It is possible for the sender to overwhelm the receiver. Hence, there is a need to control the speed of transfer. Flow control is used at the data link layer to control the data transfer process between speed incompatible nodes of a network.
• Abnormal condition recovery: Abnormal conditions such as loss of response, or failure of transfer, are handled by special functions at the data link layer. These functions detect the presence of the above said problems and recover the transmission.
• Termination: After the data transfer process is complete; the data link layer relinquishes the control of the link. This activity is known as a termination. Data link layer uses special functions for the termination process.
In LAN data link layer is divided in the 2 layers:
Logical Link Control Sublayer: The uppermost sublayer is Logical Link Control (LLC). This sublayer multiplexes protocols running atop the data link layer, and optionally provides flow control, acknowledgment, and error recovery. The LLC provides addressing and control of the data link. It specifies which mechanisms are to be used for addressing stations over the transmission medium and for controlling the data exchanged between the originator and recipient machines.
Media Access Control Sublayer: The sublayer below it is Media Access Control (MAC). Sometimes this refers to the sublayer that determines who is allowed to access the media at any one time. Other times it refers to a frame structure with MAC addresses inside. There are generally two forms of media access control: distributed and centralized. Both of these may be compared to communication between people: The Media Access Control sublayer also determines where one frame of data ends and the next one starts. There are four means of doing that: a time based, character counting, byte stuffing and bit stuffing.
We’ll be covering the following topics in this tutorial:
Services Provided To Network Layer
• Network layer is the layer 3 of OSI model and lies above the data link layer. Data link layer provides several services to the network layer.
• The one of the major service provided is the transferring the data from network layer on the source machine to the network layer on destination machine.
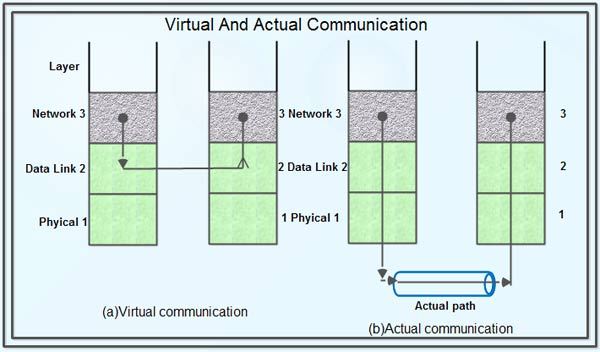
• On source machine data link layer receives the data from network layer and on destination machine pass on this data to the network layer as shown in Fig.
• The path shown in fig (a) is the virtual path. But the actual path is Network layer -> Data link layer -> Physical layer on source machine, then to physical media and thereafter physical layer -> Data link layer -> Network layer on destination machine
 The three major types of services offered by data link layer are:
The three major types of services offered by data link layer are:
1. Unacknowledged connectionless service.
2. Acknowledged connectionless service.
3. Acknowledged connection oriented service.
1. Unacknowledged Connectionless Service
(a) In this type of service source machine sends frames to destination machine but the destination machine does not send any acknowledgement of these frames back to the source. Hence it is called unacknowledged service.
(b) There is no connection establishment between source and destination machine before data transfer or release after data transfer. Therefore it is known as connectionless service.
(c) There is no error control i.e. if any frame is lost due to noise on the line, no attempt is made to recover it.
(d) This type of service is used when error rate is low.
(e) It is suitable for real time traffic such as speech.
2. Acknowledged Connectionless Service
(a) In this service, neither the connection is established before the data transfer nor is it released after the data transfer between source and destination.
(b) When the sender sends the data frames to destination, destination machine sends back the acknowledgement of these frames.
(c) This type of service provides additional reliability because source machine retransmit the frames if it does not receive the acknowledgement of these frames within the specified time.
(d) This service is useful over unreliable channels, such as wireless systems.
3. Acknowledged Connection – Oriented Service
(a) This service is the most sophisticated service provided by data link layer to network layer.
(b) It is connection-oriented. It means that connection is establishment between source & destination before any data is transferred.
(c) In this service, data transfer has three distinct phases:-
(i) Connection establishment
(ii) Actual data transfer
(iii) Connection release
(d) Here, each frame being transmitted from source to destination is given a specific number and is acknowledged by the destination machine.
(e) All the frames are received by destination in the same order in which they are send by the source.
Data Link Layer Protocols
Two major classes of protocols, widely used by the data link layer are bit-oriented protocols and character-oriented protocols.
Character-oriented Protocols
Character-oriented protocols use a predefined set of characters to convey the information. A special character set is used for the data formatting and supervising the transfer of information across the link. Different character codes have been developed. These character codes differ in length by the number of bits used. There are graphics characters, which represent symbols, control characters, which are used to control a remote terminal, and communication characters, which control computer functions such as synchronization and message handling.
The most common character-oriented code is the seven-bit ASCII code. ASCII stands for American Standard Code for Information Interchange. Every character is identified by means of a 7-bit binary code. One extra bit is added for the purpose of error detection. This bit is known as a parity bit. The number of Is in each character determines this bit. If the number of bits is even, a 1 bit is used as a parity bit, to make the total number of bits, odd. Otherwise, the parity bit is even. This process is known as odd parity. With even parity, if the number of Is in the character is odd, a 1 bit is added as a parity bit, to make the total number of Is into an even number, otherwise a zero is used as a parity bit. The ASCII character table is shown in Table 3.1. Another widely used character code is the Extended Binary Coded Decimal Interchange Code (EBCDIC). It is an eight-bit code similar to the ASCII code.
Even though character-oriented protocols are used extensively in many applications, they have number of shortcomings. Because of this, they are seldom used in modern applications.
Bit-oriented Protocols
Out of many bit-oriented protocols, some important protocols and the organizations that developed them are given below.
• High level Data Link Control (HDLC) – International Standard Organization (ISO)
• Advanced Data Communication Control Procedure (ADCCP) – American National Standard Institute (ANSI)
• Synchronous Data Link Control (SDLC) – IBM
3. HDLC Protocol Features
The following are the features of HDLC protocol.
• The protocol and data are totally independent. This property is known as transparency .
• It is suitable for a network with a variety of configurations. Examples include point-to-point, multi drop, and loop configurations.
• It supports half and full duplex operations.
• It efficiently works over links with long propagation delay and links with high data rates.
• It provides high reliability. Problems like data loss, data duplication, and data corruption do not occur.
The HDLC Protocol
Three modes of operations are defined for the HDLC protocol. They are:
• Normal Response Mode (NRM)
• Asynchronous Response Mode (ARM)
• Asynchronous Balanced Mode (ABM)
The first two modes are useful for the point-to-point and multi drop configurations. In these two modes, there is one primary station and one or more secondary stations. The primary station is responsible for the initialization of links, controlling the data flow between primary and secondary stations, error control,. and logical disconnection of the secondary stations.
In the NRM mode, the primary station, before allowing the secondary stations to start transmission, performs polling. But in the ARM mode, secondary station may start transmission without a poll.
NRM is most suitable for multi drop environments.
The ABM mode is suitable only to point-to-point configuration. Each station assumes the role of a primary and secondary, depending on the need. There is no polling in this mode. In the HDLC protocol, data is transmitted in the form of frames. The frame consists of six fields as shown in Figure .
FLAG This field is used for indicating the start and end of a frame. A special eight-bit sequence 01111110is referred as a flag. Every frame starts and ends with a flag. Since this bit, sequence could accidentally occur in the data in the information field, care must be taken to avoid the occurrence of this pattern in the useful data. In HDLC, a technique called bit stuffing performs this.
ADDRESS This field contains the address of the secondary station. This field may contain one or more 8-bit addresses. 8-bit address is used when the total number of stations exceeds 256. Other wise a two-byte address is used.
CONTROL This field identifies the function and purpose of the frame. Depending on the protocol, an 8-bit or a 16-bit control field is used.
DATA This field contains the user data to be transmitted. It can be arbitrarily long or empty.
Frame Check Sequence (FCS) Each and every frame is checked for its validity. The 16-bit FCS performs this. It identifies the errors that occur in the data during the transit. It uses a 16-bit Cyclic Redundancy Check code (CRC). The CRC code is derived from the data and control fields at the transmitter and will be sent to the receiver. The receiver again derives the CRC from the received data and control fields, and checks with the received CRC. If they differ, then it is considered as an error.
Three types of frames are used with different control fields. They are:
• Information frames
• Supervisory frames
• Unnumbered frames
The information frames carry data. Supervisory frames perform basic link control functions and the unnumbered frames are used to perform supplementary link control function.
Information Frames
The first bit of the information frame contains a O. Bits 2 to 4 provide error control and flow control. This field is known as Seq. The transmitting station sends a 3-bit modulo-8 number as a sequence number in the Seq field, along with the data. When a receiving station receives this frame, it sends the acknowledgment in the bit positions 6 to 8. This field is known as Next field. The number in the Next field denotes the next expected frame number by the receiver. This kind of acknowledgment is known as piggybacked acknowledgment. Acknowledgment may also be sent along with supervisory frame. Bit number 5 is known as Poll or Final bit, alternatively known as P IF. P mode is used by the central computer to poll terminals for sending data. Terminals, to send their final frame use F or Final mode. The supervisory and unnumbered frames also use this mode.
Supervisory Frames
The following are some of the supervisory frame functions.
Flow Control Once a station has completed the transmission of seven frames, no more frames are transmitted, until the acknowledgment for the first frame is received.
Error Control If the received frame contains error, a negative acknowledgment “NAK “is sent back to the transmitter via a supervisory frame. There are two types of protocols used for this. They are the Go back-N protocol and Selective repeat protocol. In the go-back-N mode, all the frames including the garbled ones are retransmitted. In the selective repeat mode, the sending station retransmits only the frames that contain error.
Pipelining More than one frame may be in transit at a time. This allows efficient use of links and reduces the average propagation delay.
Types of Supervisory Frames
The first bit of a supervisory frame has a value ‘1’. The second bit has a value ‘0’. Bits 3 and 4 denote the type. Bit 5 is P IF field. Bits 6, 7 and 8 are used for Next field.
There are four types of supervisory frames. The details of these are given below.
Type 0: This type of supervisory frame is known as receive read. It is an acknowledgment frame. It is used to indicate the number of the next frame expected. This supervisory frame is used when there is no frame to send for piggybacked acknowledgment. The type field of this frame contains the bit pattern ’00’.
Type 1: It is a negative acknowledgment frame known as reject. It is used to indicate that an error has occurred. The Next field indicates that the sender is requested to retransmit all the frames starting from the number specified in the Next field. The type field contains ’01’.
Type 2: The name of this supervisory frame is receive not ready. This frame informs the sender that all the frames, except the one specified in the next field, are acknowledged. It also asks the sender to stop sending. This frame is transmitted to indicate some temporary problem. The type field contains ’10’.
Type 3: This frame is known as selective reject. It calls for the retransmission of only the specified frame. The sequence number of the frame to be retransmitted is specified in the next field.
The third type of frame, whose format is given in Figure, is known as unnumbered frame. It is used for control purposes.
A specific unnumbered frame is an unnumbered acknowledgment frame. This frame is sent as acknowledgment for the loss or damaged control frames.
The Sliding Window Protocol
One important protocol used by the data link layer is the sliding window protocol. This protocol uses a stop-and-wait approach. Initially, the sender transmits a frame. The second frame is transmitted after the acknowledgment for the first frame is received from the receiver. The acknowledgment or Next field of the frame contains the number of the next frame to be received by the receiver. If this number matches with the number of the frame, the sender is trying to send, the sender discards the first frame from the buffer. Otherwise, it retransmits the same frame. The sender maintains a list of consecutive sequence numbers, corresponding to the frames it is prepared to send. This is known as a sending window. Similarly, the receiver also maintains a window for the frames it is prepared to receive. This is known as receiving window. Both windows need not have the same upper and lower bounds or even same size.
The sequence numbers within the sender’s window represent the frames already sent but not yet acknowledged. Whenever a new frame arrives, it is given the highest sequence number and advances the upper end of the window by one step. When an acknowledgment arrives, it advances the lower edge of the window by one step.
It is possible that the frames available within the sender’s window will be damaged or lost during the transit. Hence, the sender must keep copies of all frames in its memory for possible retransmission. As soon as the window reaches the maximum size, the sender stops accepting new frames for transmission.
The receiving data link layer’s window consists of the sequence number of the frame it is prepared to accept. Any frame received with sequence number outside this range is discarded. When a frame whose sequence number is equal to the lower edge of the window is received, the window is moved by one step and an acknowledgment frame is generated. Unlike the sender’s window, the receiver’s window always maintains its initial size. When the size of the receiver’s window is 1 that means the receiver is prepared to accept all frames in a sequential order.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular