The term variable-length subnet mask (VLSM) refers to the fact that a network can configure with different subnet mask. The basic idea behind VLSM is to offer more flexibility by dividing a network into multiple subnets while optimizing the allocation of varying amounts of host space between subnets. Without VLSM, only one subnet mask can apply to an entire network. It would restrict the number of hosts given the number of subnets required. If you select the subnet mask so that it has enough subnets, you might not be able to assign enough host numbers in each subnet. The same is true for hosts; A mask that allows enough hosts may not provide enough subnet space. VLSM provides the ability to assign subnets with varying numbers of hosts, allowing the network administrator to use the address space better.
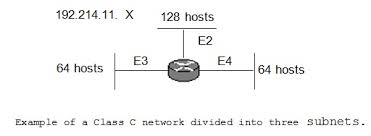
Suppose, for example, that you are assigned a class C network 192.214.11.0 and that you need to divide it into 3 subnets. One subnet requires 100 host numbers, and the other 2 require 50 host numbers each. Ignoring the limits of the two network ends (0, network number, and 255, direct broadcast address), theoretically, you have 256 host numbers available, from 192.214.11.0 to 192.214.11.255. As we will see, the desired subnetting cannot be carried out without VLSM.
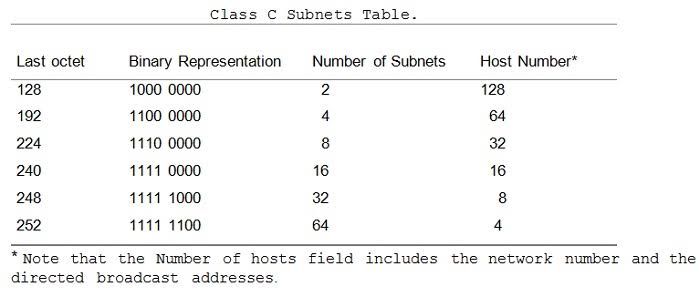
To determine the available subnet options associated with the 192.214.11.0 network, you first need to identify the netmask, which in the case of this traditional class C network is represented by 255.255.255.0 (all one in the first 3 octets). A handful of subnet masks of the form 255.255.255.X can be used to divide the class C 192.214.11.0 network into more subnets. A mask must have an endless number of bits 1, starting with the leftmost bit, while the remaining bits must be 0.
The table lists the potential subnet size that could be used to segment the 256 addresses available on additional subnets.
Before VLSM, a traditional network would have been divided using a single contiguous network mask over the entire network. In this case, you have the option to use a mask 255.255.255.128 and divide the address into two subnets with 128 hosts each, or use 255.255.255.192 and divide the addresses into four subnet size with 64 hosts each. None of these options meet the requirement of having 100 hosts in one segment and 50 hosts in each of the other two.
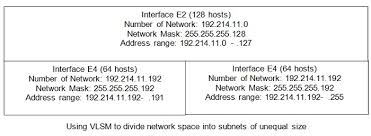
Using masks of variable length, the established objectives can achieve. For example, suppose your network is 192.214.11.0. First, use mask 255.255.255.128 to divide the network address into two subnets with 128 hosts each. These two subnets are represented by 192.214.11.0. (.0 to .127), the lower half of the Class C network, and 192.214.11.128 (.128 to .255), the upper half of the class C network. Then, subdivide the 192.214.11.128 network using the mask 255.255.255.192, creating two subnets with 64 hosts each: subnet 192.214.11.128 (.128 to .191) and subnet 192.214.11.192 (.192 to .255). Figures illustrate how to divide the address space similarly (note that the network number and the directed broadcast addresses included in the total hosts).
Of course, not all routing protocols can support VLSM. The routing information protocol, version 1 (RIP – 1) and the internal gateway routing protocol (IGRP) do not carry network masks in routing updates and, therefore, cannot correctly deal with variably subnetted networks. Currently, even with the appearance of routing protocols such as First Shortest Free Route (OSPF), Enhanced IGRP (EIGRP), Routing Information Protocol, version 2 (RIP-2), and Intermediate System-Intermediate System (IS -IS), which support VLSM, administrators still have difficulty adapting to this technique.
Most of the first networks built on RIP-1 and IGRP do not have their IP addresses assigned so that they can be grouped in blocks more optimally. Instead, their IP addresses are scattered, and administrators have to re-number their hosts to comply with the new addressing scheme. Such renumbering is painful, and managers often consider it misplaced. This coexistence is a challenge, and administrators have resorted to many maneuvers and static routing to host it.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular