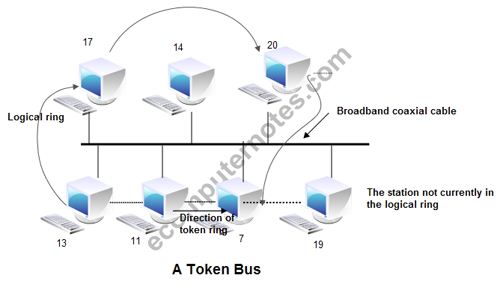
IEEE 802.4 Token Bus: In token bus Computer network station must have possession of a token before it can transmit on the computer network. The IEEE 802.4 Committee has defined token bus standards as broadband computer networks, as opposed to Ethernet’s baseband transmission technique. Physically, the token bus is a linear or tree-shape cable to which the stations are attached.
The topology of the computer network can include groups of workstations connected by long trunk cables. Logically, the stations are organized into a ring. These workstations branch from hubs in a star configuration, so the network has both a bus and star topology. Token bus topology is well suited to groups of users that are separated by some distance. IEEE 802.4 token bus networks are constructed with 75-ohm coaxial cable using a bus topology. The broadband characteristics of the 802.4 standard support transmission over several different channels simultaneously.
When the logical ring is initialized, the highest numbered station may send the first frame. The token and frames of data are passed from one station to another following the numeric sequence of the station addresses. Thus, the token follows a logical ring rather than a physical ring. The last station in numeric order passes the token back to the first station. The token does not follow the physical ordering of workstation attachment to the cable. Station 1 might be at one end of the cable and station 2 might be at the other, with station 3 in the middle.
In such a case, there is no collision as only one station possesses a token at any given time. In token bus, each station receives each frame; the station whose address is specified in the frame processes it and the other stations discard the frame.
We’ll be covering the following topics in this tutorial:
Physical Layer of the Token Bus
The conventional 75 ohm coaxial cable used for the cable TV can be used as the physical layer of the token bus. The different modulation schemes are used. They are, phase continuous frequency shift keying, phase coherent frequency shift keying, and the multilevel duo binary amplitude-modulated phase shift keying. Signal speeds in the range 1 Mbps, 5 Mbps, and 10 Mbps are achievable. The physical layer of the token bus is totally incompatible to the IEEE 802.3 standard.
MAC Sublayer Function
• When the ring is initialized, stations are inserted into it in order of station address, from highest to lowest.
• Token passing is done from high to low address.
• Whenever a station acquires the token, it can transmit frames for a specific amount of time.
• If a station has no data, it passes the token immediately upon receiving it.
• The token bus defines four priority classes, 0, 2, 4, and 6 for traffic, with 0 the lowest and 6 the highest.
• Each station is internally divided into four substations, one at each priority level i.e. 0,2,4 and 6.
• As input comes in to the MAC sublayer from above, the data are checked for priority and routed to one of the four substations.
• Thus each station maintains its own queue of frames to be transmitted.
• When a token comes into the station over the cable, it is passed internally to the priority 6 substation, which can begin transmitting its frames, if it has any.
• When it is done or when its time expires, the token is passed to the priority 4 substation, which can then transmit frames until its timer expires. After this the token is then passed internally to priority 2 substation.
• This process continues until either the priority 0 substation has sent all its frames or its time expires.
• After this the token is passed to the next station in the ring.
Frame format of Token Bus
The various fields present in the frame format are
1. Preamble: This. Field is at least 1 byte long. It is used for bit synchronization.

2. Start Delimiter: This one byte field marks the beginning of frame.
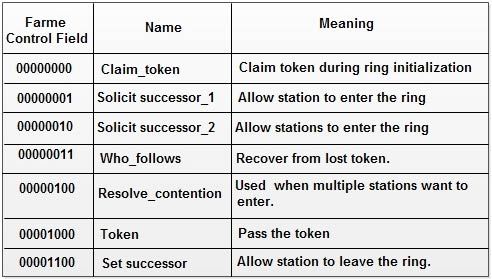
3. Frame Control: This one byte field specifies the type of frame. It distinguishes data frame from control frames. For data frames it carries frame’s priority. For control frames, it specifies the frame type. The control frame types include. token passing and various ring maintenance frames, including the mechanism for letting new station enter the ring, the mechanism for allowing stations to leave the ring.
4. Destination address: It specifies 2 to 6 bytes destination address.
5. Source address: It specifies 2 to 6 bytes source address.
6. Data: This field may be upto 8182 bytes long when 2 bytes addresses are used & upto 8174 bytes long when 6 bytes address is used.
7. Checksum: This 4 byte field detects transmission errors.
8. End Delimiter: This one byte field marks the end of frame.
The various control frames used in token bus are:
Maintaining the Ring
Control frames Control frames are frames used for controlling and maintaining the logical ring. The format is same as the format specified in Figure, except the presence of an info field. There are different bit patterns used in the frame control field to define different types of control frames. Some important ring-maintaining activities are discussed below.
Adding a new station To add a new station to the logical ring, the station which currently holds the token broadcasts periodically sends a special control frame called a Solicit-successor frame. This frame contains the address of the sending station and its successor. This intimates the stations within the specified range to join the ring. Hence, the ring remains sorted.
Leaving the logical ring A station can simply leave the ring by sending its successor address to its predecessor and asks it to set this as its successor. To perform this, it passes a special control frame called set successor. The frame contains the address of predecessor as destination address and the address of the successor as sending address.
Ring initialization When the network is powered on, initially, all the stations are off. As soon as the first station is initiated, it checks the channel for the presence of any contenders, by sending a special control frame called claim-token. If there is no response, it generates a new token; thereby, creating a new logical ring with a single station. Periodically it transmits solicit successor tokens, hence, new stations are added frequently, making ‘the logical ring grow.
Failure of a successor station When a station finishes the transmission, it passes the token to the next station (successor). If the successor station fails to claim the token, then other stations in the network may not be able to claim the token. Allowing stations to watch their successor’s activity after passing the token to them, can rectify this problem. If nothing takes place, until a predetermined time, it retransmits the token. If again there is no response, the successor station is disconnected from the logical ring and a new control frame set-successor is sent to the successor of the failed station.
Failure of multiple successors If a station is not able to pass the token to its successor, or if the successor of its successor also failed, then it sends a special control frame called solicit successor-2, to check the availability of other stations on the network. The network is then relatively established, by running the contention algorithm for the second time.
Failure of token holder If the token holder fails, none of the other stations can get the token. Each station in the ring has a timer internally. They wait until the timer expires and transmits a claim-token frame, and the network is reestablished.
Multiple tokens If the token holder detects the transmission of frames from some other station, it discards its token. If multiple tokens are present in the network, the above process is repeated until only one token is present in the network. If all the tokens in the network are discarded, then one or more stations transmit claim-token frame, and restart the network activity.
The Token-passing Bus Protocol functions
The following functions provided by the token bus protocol.
• Ring initialization performed when the network is first powered up and after a catastrophic error.
• Station addition optionally performed when a station, holding the token accepts the insertion of a new successor station, (that is, a new station with an address) that is between that of the station holding the token and its current successor station.
• Station removal is achieved by sending new successor identification to its predecessor, or by just disconnecting from the LAN. In the latter case, recovery mechanisms establish the proper new logical ring configuration.
• Recovery and Management, including recovery from failures such as bus idle (lack of activity on the bus) token-passing failure (lack of valid frame transmission), the presence of duplicate token, and detection of a station with a faulty receiver.
When the network is first powered up, or after a catastrophic error, the logical ring needs to be initialized. The idle bus timer, expiring in a LAN station, triggers this process. The detecting station sends a Claim Token MAC control frame.
As described above, each participating station knows the address of its predecessor (the station that transmitted the token to it and its successor) and station to which the token should send next. After a station has completed transmitting data frames and has completed other logical ring maintenance functions, the station passes the token to its successor by sending it a token MAC control frame. Any failure in reaching a successor station triggers a staged recovery mechanism, using other MAC control frames (set solicitor 1and set solicitor 2). If the token holder does not receive a valid token after sending the token the first time, it repeats the token pass operation. If the successor does not transmit after a second token frame, the sender assumes that its successor has failed and sends a Who Follows the MAC control frame, containing its successor’s address in the data field. The station, detecting a match between its predecessor and the address in the Who Follows frame data field, respond by sending its address in a Set Successor MAC control frame. In this way, the token holding station establishes a new successor, excluding the failing station from the logical ring. Stations are added to the logical ring through a controlled contention process, using response windows, a specific interval of the time typical to all stations, and based on numerical address comparisons. The actual procedure referred to as the Solicit Successor Procedure.
This procedure raises a concern concerning excessive delay experienced by a station before gaining access to the LAN when many stations attempt to insert into the logical ring and perform the solicit successor procedure. The time a station has to wait between successive passes of the token is called the token rotation time (TRT).To avoid excessive TRT, every station measures the rotation time of the token. If the time exceeds a predefined value set by the station management, the station defers initiation of the solicit successor procedure and verify, at the next appearance of the token, whether it is now rotating fast enough to perform the procedure.
A station can remove itself from the logical ring only by not responding anymore to the token passed to it. Ring station sequence recovery procedures adjust the successor and predecessor information in the predecessor and successor stations, respectively. A more efficient way of leaving the logical ring is to have the exiting station send a Set Successor MAC control frame to its predecessor, containing the address of its successor.
Access priority The token-passing bus protocol provides an optional8-level priority mechanism by which higher layer data frames, LLC sublayer or higher-level protocols, are assigned to eight different service classes, according to their desired transmission priority. Service classes range from 0 (low) to 7 (high). The purpose of this priority mechanism is to allocate bandwidth to the higher priority frames and to send lower priority frames only when there is sufficient bandwidth left. Similarly, each access class is assigned a target token rotation time (TTRT).
Each station measures the time it takes the token to circulate the logical ring. If the token returns to a station in less than the target token rotation time, the station can transmit more frames until the expiration of the TTRT. If the token takes more than the TTRT for a specific priority level, no frames of this priority class can send at this pass of the token.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular