Network architecture understood as the set of layers and layer protocols that constitute the communication system.
Network architectures offer different ways of solving a critical issue when it comes to building a network: transfer data quickly and efficiently by the devices that make up the network. The type of network architecture used will not only determine the network topology but also define how network nodes access those media. There are different types of network architecture, all of them with their strategy to conduct information over the network.
Network Architecture defines the communications products and services, which ensure that the various components can work together. In the early days of data communication systems, the majority of communications were between the DTE and the host computer. Therefore, transmission control procedures were alone enough as communication protocols. However, recent computer systems link with other systems to form a network which result in a situation where different protocols serving different purposes are required. Hence, the network architecture represents a systemization of the various kinds of protocols needed to build a network.
Computer manufacturers have developed different protocols as needed. This means that each type of computer needed to support different protocols. This necessitated large development and maintenance costs. All computer manufacturers, worked together to standardize and systemize protocols to link their models and reduce the development and maintenance costs thereby. This was how each manufacturer built their own network architecture.
Since the concept of the network architecture was first introduced, connecting computers of the same Manufacturer has become easier. However, from user’s perspective, the ideal form of network architecture is one which enables machines of all manufacturers to connect to each other. Therefore, the need of standardization of network architecture arose.
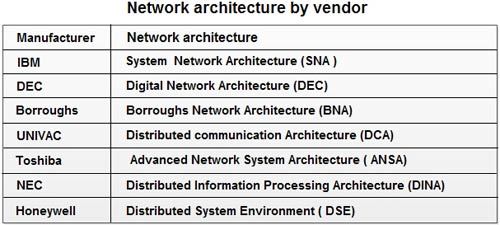 Following are the ways to achieve connection between different manufacturers:
Following are the ways to achieve connection between different manufacturers:
- Protocol Converters These are devices that translate from one native protocol into another, for example, from ASCII to IBM SNA/SDLC.
- Gateways These are hardware/software combinations that connect devices running different native protocols. In addition to protocol conversion, gateways provide a gateway connection between incompatible networks. Examples include Ethernet-to-Token Ring gateways, X.25-to- Frame Relay gateways, and T-carrier-to-E-Carrier International Gateway Facilities (IGFs).
In addition to the above, Protocol Analyzers are available as diagnostic tools for displaying and analyzing communications protocols. Analyzers allow technicians, engineers and managers to test the performance of the network to ensure that the systems and the network are functioning according to specifications. LAN managers, for instance, use protocol analyzers to perform network maintenance and troubleshooting and to plan network upgrades and expansions.
Types of Network Architecture
Ethernet
Ethernet is the most used network architecture today. Ethernet provides network access using multiple cover perception access with collision detection or CSMA / CD (carrier sense multiple access with collision detection). This network access strategy is basically that each component of the network or node listens before transmitting the information packets. If two nodes transmit at the same time, a collision occurs. When a collision is detected, the computer interrupts the transmission and waits for the line to be free. One of the computers then goes on to transmit the data, achieving control of the line, and complementing the transmission of the packets.
Ethernet is a passive wait and listens to architecture. Collisions between packets are often frequent on the network and computers have to dispute the transmission time. Ethernet networks are usually implemented in bus or star configurations, depending on the type of medium used for the network connection. One of the most common Ethernet implementations (used with different types of media) is the one that works at 10Mbps. This 10 Megabit Ethernet that runs with twisted pair cables is called 10BaseT: 10 indicates the transmission speed in megabits per second; the term Base which is a transmission in base-band (the base is nothing more than a sequence of bits, or a digital flow of information); and the T is the letter used to abbreviate the twisted pair cable.
When the packets are ready for transmission over the cable, their final form is called a frame. Ethernet uses, in fact, several types of frames, which can cause problems in the network if all the nodes have not been configured to use the same type of frame. These are the different types of frames that Ethernet uses:
• 802.3 Ethernet: Although this frame has the relevant IEEE number, it does not meet all Ethernet specifications. Novel Netware 2.2 and 3.1 networks use this type of frame.
• 802.2 Ethernet: This type of frame meets all the specifications dictated by the IEEE. It found in the latest versions of Novell Netware, including Netware 3.12, 4.x and 5.x.
• Ethernet SNAP: This type of Ethernet frame is the one used by Apple Talk networks.
• Ethernet II: Networks that run several protocols such as the Internet generate Ethernet II frames.
Although 10 Megabits Ethernet networks were the most used until recently, they increasingly replaced by Fast Ethernet or Fast Ethernet (100 Mbps) and Gigabits (1000Mbps or 1Gbps). Both versions of Ethernet require category 5 twisted pair cables as well as unique network cards and hubs (Gigabit Ethernet often uses category 6 twisted pair cables).
The main advantage of Ethernet refers to the low cost of implementing such a network architecture. The NICs, cables, and hubs that used are quite economical compared to the hardware required by other architectures such as Token Ring. As for its disadvantages, the worst of all has to do with the number of collisions that occur. And it is already known: the more collisions that occur in a network, the more slowly it run, and may even cause the whole network to fall.
Token Ring
IBM Token Ring is a faster and safer network that uses the signal token as a strategy to access the communication channel. Token Ring networks connected in a star-shaped topology through a Multistation Access Unit (MAU) that provides the central connection for the nodes of the network. The ring through which the signal or token circulates (the token travels in only one direction) is a logical ring included within the MAU.
The token circulates through the ring until it is picked up by a computer that wants to send information over the network. The computer that passes the token to the next computer included in the logical ring is called the nearest active upstream neighbor or NAUN. For its part, the computer that receives the signal or token is known as the nearest active downstream neighbor or NADN.
After taking the token and transmitting the data, the computer generates a new token and passes it to your NADN. If it does not have to transmit data, the token goes back through the ring waiting for a node in the network to capture it to send information.
The Token Ring architecture is characterized by not causing data collisions and offers the same level of access to the communication channel to all nodes included in the network. It is slower than other Ethernet implementations (Token Ring can work at maximum speeds between 4 and 16Mbps), but the network degrades more smoothly during a possible overload of the system.
Token Ring also offers some fault tolerance thanks to its error detection strategy called beaconing. When computers connected to the network for the first time, the first one that is turned on becomes the active Monitor. The active monitor is responsible for sending, every seven seconds, a packet of data that travels through the ring to help determine if any node does not work correctly. For example, if a computer does not receive the package sent to you by your NAUN, it creates a package that includes your address and that of the NAUN and sends it to the network. Since it includes all relevant information, the Token Ring can use it to reconfigure the ring and maintain traffic on the network automatically.
FDDI
The Fiber Distributed Data Interface (FDDI) is an architecture that provides a high speed and high capacity environment that can be used to connect several different types of networks (see Figure). FDDI uses fiber optic cables and configured in a ring topology. FDDI uses the signal or token pass as a method of access to the communication channel and can operate at high speeds (almost all implementations work at 100Mbps, but data can also transfer at higher speeds).
Since FDDI uses a token pass strategy to access the data channel, it does not pose security problems and provides the same level of access to all nodes connected to the network. With FDDI, priority levels can also be specified, although network servers can always send more data frames than client computers.
Since FDDI uses an authentic ring topology, breakages in the wiring system can pose serious problems. To build a fault tolerance within an FDDI network, a second ring used. And so, when a computer cannot communicate with its nearest previous neighbor, it goes on to send the data to the second ring (which conducts the data in the opposite direction to the one used by the first ring).
Logically, FDDI implementations require a special NIC card. Dual connection stations (where computers connected to the two rings of the network) use a network card that connects them to the two rings of the upper communication channel. Instead of using hubs, hubs are used to connect the LAN nodes to the FDDI network. Since these computers not directly coupled to the FDDI ring, they only require a NIC connection to connect to the hub.
AppleTalk
AppleTalk is the network architecture used by Apple Macintosh computers. The network hardware required in this case already installed on each Macintosh (although, if you want to connect a Macintosh to an Ethernet network, you need an Ethernet network card for Mac). The wiring system that allows Macintosh computers to connect is called local talk and uses twisted pair cables with a special adapter for Macintosh.
AppleTalk uses a unique addressing system to determine the address of the nodes included in the network. When a Macintosh connected to the network is turned on, that computer generates a random address and transmits it over the network. This random address becomes your network address (provided that no other Macintosh computer uses that same address; otherwise, the computer have to continue generating random addresses until it finds one that has not used).
AppleTalk is quite similar to Ethernet since it is also a passive network architecture. AppleTalk uses the CSMA / CA method (Carrier Sense Multiple Access with Collision Avoidance or Multiple Cover Perception Access with collision avoidance), in which computers listen to the network to determine if the communication channel occupied. Once verified that the channel is free, the computer sends the packet to the network letting the rest of the computers know its intention to transmit data. The fact that the computer notifies the rest of the network nodes of its intention to transmit data substantially reduces the number of possible collisions in a particular CSMA / CA network when compared to Ethernet. These packet announcements, however, tend to slow down the network speed, which is not very desirable since Macintosh networks only work with transmission speeds of 230.4Kbps. The good thing is that by having the hardware and software necessary to connect to the network installed, Macintosh computers provide a secure and economical way to connect several workstations in order to share files or a printer.
 Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular
Dinesh Thakur holds an B.C.A, MCDBA, MCSD certifications. Dinesh authors the hugely popular